Web Application Firewall vs. Container Firewall
How is a Container Firewall Different Than a Web Application Firewall?
By Gary Duan
Application containers provide an efficient way to deploy and manage applications, including web facing ones. But with containerization, securing applications has become even more challenging. I often get asked for the comparison of a web application firewall vs. container firewall. I also get asked about next generation firewalls (NGFW) vs container firewalls, and you can read this comparison here.
 The short summary is that web application firewalls are special function devices or software designed to protect external access to web facing applications, while in contrast container firewalls protect all internal east-west traffic between containers while also including some of the protections of a WAF. Container firewalls also contain many other features, as discussed at the last section Continuous Container Security.
The short summary is that web application firewalls are special function devices or software designed to protect external access to web facing applications, while in contrast container firewalls protect all internal east-west traffic between containers while also including some of the protections of a WAF. Container firewalls also contain many other features, as discussed at the last section Continuous Container Security.
Protecting applications in a modern rapid deployment process requires security to be built into the entire cycle, from build, to ship, to run. Code scanning and image vulnerability scanning tools should be used before containers are even deployed to production. In a production environment, a combination of traditional security tools should be deployed with cloud-native container security tools.
The move from monolithic applications to microservices creates different network patterns and new security issues. It is difficult for traditional firewalls and web application firewalls to see east-west internal traffic within a host or between hosts, especially in a container environment with constant changes as containers launch and disappear. So are NGFWs and WAFs not needed for protecting containers?
It is still critical to protect applications from attacks with the use of network firewalls and dedicated web application firewalls. In the diagram below, the NGFW provides multi-protocol inspection and protection from untrusted networks. In addition, a WAF protects external facing web front-end applications from external client attacks. The WAF provides specialized protection against the most common attacks against web applications.
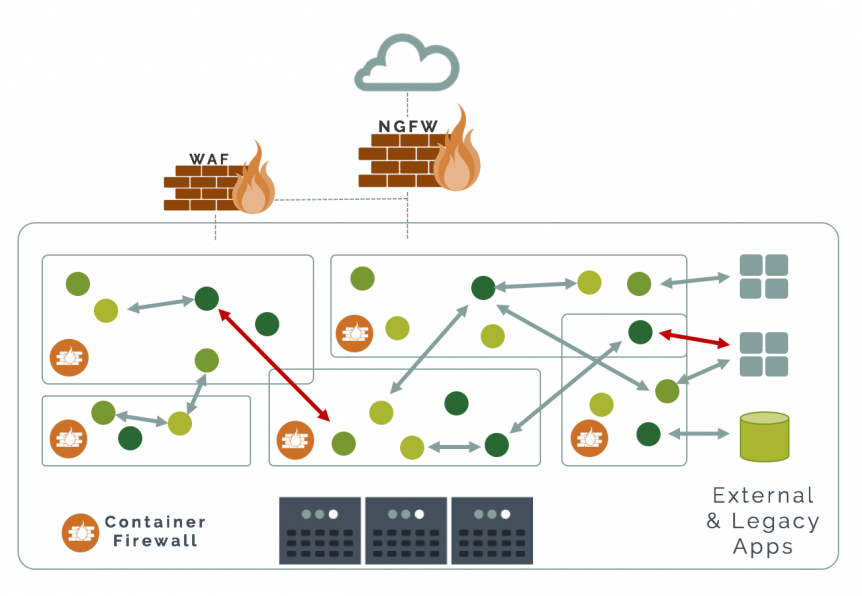
However, because monolithic web applications are now being migrated to client facing containers (services) with potentially tens or hundreds of back end services, additional layers of security from a container firewall are required. Containers are designed to be deployed in seconds and an orchestration system can launch new containers on the same hosts or across hosts depending on service demands and host resources available. Each container has its own mapped network interfaces which get assigned and deallocated on the fly. Containers can also use different protocols and ports than standard HTTP to communicate, making it critical to have both network and application security features.
Features of a Container Firewall
 A container firewall inspects and protects all traffic into and out of containers. It is able to protect cloud-native workloads, application stacks, and services. A container firewall must also protect the ingress and egress from external networks and legacy applications to containers, unlike a WAF which protects web based client access to a front-end application.
A container firewall inspects and protects all traffic into and out of containers. It is able to protect cloud-native workloads, application stacks, and services. A container firewall must also protect the ingress and egress from external networks and legacy applications to containers, unlike a WAF which protects web based client access to a front-end application.
Here are the key features of a Container Firewall:
- Cloud-native. Understands orchestration and container platform services (dns, load balancers), deployment models (e.g. services, pods, replications), network overlays, namespaces etc.
- Application intelligence. Learns the intent of applications from meta-data and behavioral analysis. Characteristics include:
- Application based (Layer 7) protocol inspection and protection. Does not use IPtables or only L3/L4 rules.
- Recognize and enforce policy based on popular application protocols such redis, mysql, mongodb.
- Whitelist based, automatically updating rules. Discovers application behavior and security requirements and adapts to changes and updates.
- Integrates with container orchestration. Scales across hosts, clouds and adapts to updates.
- Container threat protection. Protects against common application level attacks such as DDoS, DNS attacks. Many of these protections are also found in web application firewalls.
- Blacklist and custom rules. Ability to set rules based on container labels, IP addresses, ranges, or other L3/L4 policies.
- Other host security and auditing features. See the last section on Continuous Container Security.
- CI/CD integration. Automate the deployment and management to fit within a continuous integration and delivery pipeline.
Because a container firewall is meant to primarily protect container traffic, it is not meant to replace the NGFW, IDS/IPS, or WAF at the edge. However, it must protect against common known application attacks which could originate internally.
Features of a Web Application Firewall (WAF)
Web application firewalls provide advanced protection for web-based traffic, typically HTTP/S where traffic from the internet first interacts with the ‘front-end’ of an application. Most WAFs detect a number of application threats including the OWASP Top 10.
In general, a web application firewall will include these features:
- Detect Application Attacks. Detect SQL injection, Cross-site scripting (XSS), DDoS, DNS attacks etc.
- Protocol, Logic, and Object Format Support. JavaScript, SQL, HTML, XML, JSON, Cookies, etc.
- Support HTTP and HTTPS. Some WAFs will terminate SSL connections, while others rely on termination by a load balancer in front.
- Virtual Patching. Temporarily ‘patch’ vulnerabilities with network blacklist policies until application can be patched.
Chart: WAF vs Container Firewall Comparison
| Web Application Firewall (WAF) | Container Firewall | |
|---|---|---|
| Functions |
|
|
| Deployment |
|
|
| Integration |
|
|
*See below for other container security features
Continuous Container Security
A container firewall solution can provide not only network based application protection but also many other features. Because container firewalls are distributed on hosts they can provide host security and auditing as well. By integrating with the Docker engine and orchestration platforms a container firewall can provide process inspection, security auditing, and resource monitoring. Here are some other features to look for:
- Host and container process monitoring to detect privilege escalations and suspicious processes
- Vulnerability scanning (registries, hosts, containers)
- Security testing with Docker Bench and CIS benchmarks for auditing and compliance.
The shift to container based applications requires new security technology to secure containers. Comparing web application firewalls vs. container firewalls is interesting, but the best security is a layered strategy which uses both to secure different parts of the infrastructure.
About the Author: Gary Duan
Gary is the Co-Founder and CTO of NeuVector. He has over 15 years of experience in networking, security, cloud, and data center software. He was the architect of Fortinet’s award winning DPI product and has managed development teams at Fortinet, Cisco and Altigen. His technology expertise includes IDS/IPS, OpenStack, NSX and orchestration systems. He holds several patents in security and data center technology.
Related Articles
Feb 01st, 2023
DevOps Transformation
Oct 25th, 2023
What is Container Security?
Jul 22nd, 2022
SUSE Rancher Manages Amazon EKS Hybrid Landscape
Feb 01st, 2023