SUSE Private Registry: A safe Harbor for your containers.
SUSE has been working on an exciting project that we are now ready to share with a wider audience! SUSE Private Registry (powered by Harbor 2.1) provides a central component of a cloud native application delivery platform. It is an OCI registry for storing, replicating, managing and securing Open Container Initiative (OCI) images and artifacts.
SUSE Private Registry is deployed on Kubernetes using Helm and provides a trusted, reliable, and highly available image artifact repository. It has been tested on SUSE CaaS Platform versions 4.2 and 4.5, K3s, and managed Kubernetes services like Azure Kubernetes Service (AKS), and Amazon Elastic Kubernetes Service (EKS). It should work on all CNCF certified Kubernetes distributions, version 1.17 or newer.
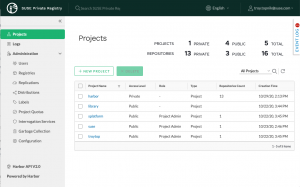
Harbor Projects
SUSE Private Registry is based on the Harbor CNCF project and includes theming, testing, security hardening, and maintainability improvements from SUSE’s Cloud Solutions Ecosystem Team.
Why a Private Registry?
If you’ve been using containers for a while, you’ve probably worked extensively with public registries like Docker Hub. They’re easy to use, and mostly free, so it’s easy to become dependent on them.
The recent introduction of rate limiting on Docker Hub woke a lot of people up to just how much data they were pushing to and pulling from this registry. Maybe you have CI/CD systems that are constantly pulling the same container images for builds, or maybe you’re not cleaning up older unused images. You know you should run your own registry locally, but you’ll miss the nice UI, access control, and other features.
It’s possible to run your own private registry and still have those nice things. You can even configure projects in your registry to be proxy caches of the public registries you’ve been using.
Why Harbor?
We know a number of SUSE customers are interested in running their own registry, but they want a bit more than just a bucket for their images. Fans of the Portus project will know that SUSE had already created a beautiful interface and useful features for self-hosted private registries, and might wonder why we based SUSE Private Registry on Harbor instead.
Before embarking on development, we carefully evaluated the main open source registry projects, including Portus. Portus is still a viable registry interface, but we were impressed by the breadth of features in Harbor and saw a thriving community behind it. With Harbor’s recent graduation from the CNCF incubator we felt it was the best choice for our enterprise customers moving to Kubernetes.
Features
Harbor provides secure replication, storage, and access to OCI artifacts using policies and role-based access control. SUSE Private Registry:
- integrates with security and vulnerability analysis tools to ensure that any image being served is free from vulnerabilities,
- provides strong project isolation, preventing access or modification of images that are not explicitly public,
- has an extensible API which you can explore through a Swagger interface, and
- compliments other SUSE web interfaces such as Stratos Console.
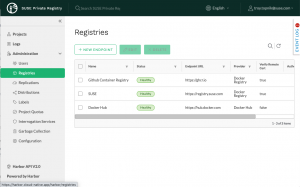
Registries & Replication
Use it for on-premise installations in network isolated environments to provide local mirroring (replication) of individual images, groups of images (e.g. a registry namespace), or entire registries. Project owners control features like automated security scanning, webhooks, and image retention policies. Admins set user permissions, project storage quotas, and a CVE allowlist globally.
Having local copies of commonly used container images speeds up deployment times on your Kubernetes clusters. Setting up a pull through cache is a single configuration option when creating a new project. We see tremendous potential for using SUSE Private Registry for improving resiliency and efficiency in data center, cloud, or edge environments.
Security Scanning
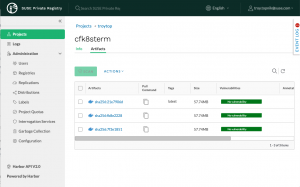
OCI image scanning via Trivy
SUSE Private Registry provides integration points for container content vulnerability scanning services. Included by default is Trivy, a simple and comprehensive scanner that can search image contents for vulnerabilities in OS packages (for SLES, openSUSE, Alpine, RHEL, CentOS, Debian, and others) as well as many language/framework package managers (like Bundler, Composer, Pipenv, Poetry, npm, yarn, and Cargo).
Notary Service
Do you want to enforce security at the container engine level? SUSE Private Registry includes Notary so you can use it as your content trust server to sign images, then enforce runtime verification with clients.
Part of SUSE Cloud Application Platform
If you have Kubernetes at your disposal it’s easy to try out SUSE Private Registry. Just follow the instructions in the documentation to configure and install it using Helm. If it’s a good fit for your organization, support is available through a subscription to SUSE Cloud Application Platform.
Related Articles
May 17th, 2022
No comments yet