SUSE CaaS Platform: System-wide Certificates
With SUSE CaaS Platform 3, it is now possible to manage self-signed certificates through the Velum UI. In this blog post, we will explain what these certificates are, why they are needed and how to use them.
What are system-wide certificates?
When bootstrapping a new cluster or managing an existing one, a new setting is available called system-wide certificates. As their name suggests, certificates entered with this mechanism are picked up by all tools that use certificates running directly[1] on the system.
In our case, this means all applications that use the certificate bundles found in the default locations for certificates: /etc/ssl/* or /var/lib/ca-certificates/*.
Why are system-wide certificates needed?
System-wide certificates were introduced in SUSE CaaS Platform 3 to allow access to any on-premise service that is secured by self-signed certificates from the cluster nodes.
One use case is the deployment of SUSE CaaS Platform on a self-hosted OpenStack instance that uses self-signed certificates. If the self-signed certificate is not distributed throughout the cluster, it would prevent Kubernetes from working: the Cloud Provider Integration (CPI) would not be able to connect to the OpenStack endpoints and that would prevent the Kubelet service from starting.
Another use case can be an internally deployed SUSE Enterprise Storage.
To allow using the SUSE CaaS Platform in this scenario, a new option was added to SUSE CaaS Platform 3 and the following section will explain how to use it.
How to use system-wide certificates
When installing self-signed certificates into Velum, it is easiest to use the ASCII (Base64) armored representation, that encodes the binary format of the certificate as text – also referred to as the PEM format.
First you have to obtain the certificate from the self-signed application.This can be done using the openssl command and connecting to the endpoint of the application. In the case of a SUSE OpenStack Cloud deployment, for example, this would be the keystone url:
echo | openssl s_client -connect keystone_endpoint:443 -showcerts 2>/dev/null | sed -n -e '/BEGIN\ CERTIFICATE/,/END\ CERTIFICATE/ p'
This will print all certificates between the -----BEGIN CERTIFICATE----- and -----END CERTIFICATE----- blocks[2].
These can be copied directly into the Velum UI for adding system-wide certificates.
There are two possible ways to add these certificates:
- During setup of the cluster
- After performing a bootstrap in the Settings menu
When deploying SUSE CaaS Platform on an OpenStack Cloud it is recommended to add the certificate during the setup to prevent an initial bootstrap failure.

Adding a certificate during cluster setup
If a certificate needs to be installed after a cluster has already been deployed, this can be done in the Settings UI, using the same forms:
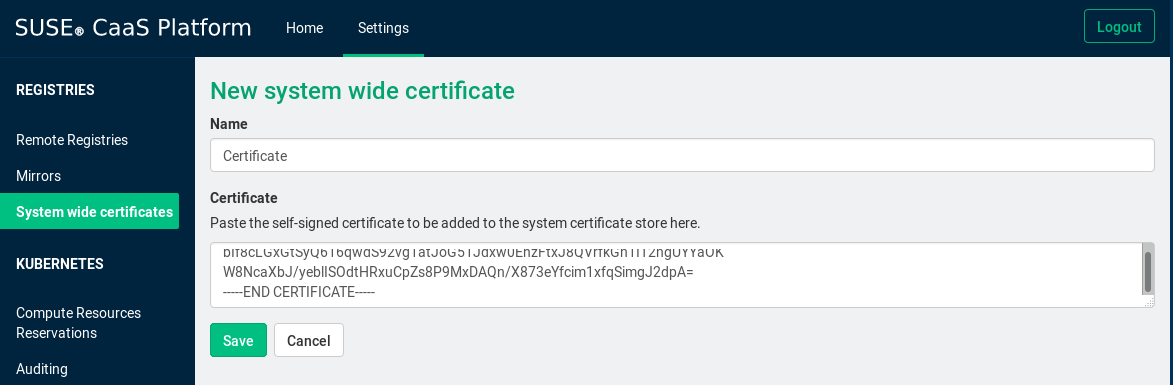
Adding a certificate in the settings
Once the changes have been propagated to the cluster, the certificates should be available for all machines.
If, after installing the certificates through Velum, an application on a cluster node fails with certificate errors, this might indicate that it does not use the system certificate stores.
[1] Certificates installed in this manner will not be directly available in your containers. If the certificates are to be used in containers, they should be made available as secrets.
[2] If there are multiple certificates printed, make sure to add all of them, as the client must be able to verify the complete certificate chain.
Related Articles
Feb 15th, 2023
Stop the Churn with SUSE eLearning
Oct 25th, 2022
SUSE Edge 2.0: A Cloud Native Solution to Manage Edge
Jun 14th, 2023
No comments yet