Achieving PCI Compliance for Containers
Although microservices and containers are not explicitly mentioned in PCI-DSS for PCI compliance, organizations implementing these technologies must focus carefully on monitoring, securing, and governance.
Microservices and containers offer some unique characteristics that support pci compliance. For example, microservices emphasize an architecture with one function per service/container. This aligns well with PCI-DSS 2.2.1, implementing only one primary function per server. Similarly, containers by design offer reduced functionality, aligning with PCI-DSS 2.2.2, enabling only necessary protocols and services.
At the same time, other aspects of microservices and containers make pci compliance a significant challenge. For example, the ephemeral nature of containers – potentially only “living” for a few minutes – means monitoring must be real-time and embedded to monitor and enforce all container activity. Plus, most container traffic is east-west in nature – versus north-south – meaning traditional security controls never see most container activity.
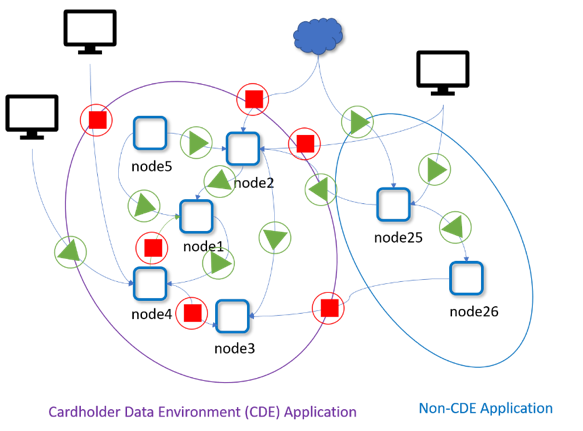
Finally, as containers come and go, so too does the scope of the Cardholder Data Environment (CDE). A continually changing CDE scope may be one of the most significant impacts of containers on monitoring and maintaining PCI-DSS compliance. As shown in the figure below, organizations must have visibility and control to define the in-scope CDE tightly. Without an advanced deep packet inspection (DPI) container firewall like NeuVector’s MultiVector container firewall, organizations implementing containers may have to consider the entire microservices environment in-scope! With Container DLP to detect unauthorized transmission of credit card PAN data, NeuVector helps ensure PCI compliance.
Watch the PCI-DSS for Containers Webinar
CyberEdge Senior Consultant Ted Ritter covers the recent PCI requirements as they relate to containers.
Download the PCI Guide
Download the complete guide to PCI Compliance with NeuVector. This report describes how NeuVector helps organizations comply with the Payment Card Industry Data Security Standard (PCI-DSS) version 3.2.1, issued in May 2018.
This guide covers the following critical PCI-DSS requirements which are affected by Docker and Kubernetes containers:
1.0 – Install and maintain a firewall configuration to protect cardholder data
2.0 – Do not use vendor-supplied defaults for system passwords and other security parameters
3.0 – Protect stored cardholder data
4.0 – Encrypt transmission of cardholder data across open, public networks
5.0 – Protect all systems against malware and regularly update anti-virus software or programs
6.0 – Develop/Maintain Secure Systems and Applications
7.0 – Restrict access to cardholder data by business need to know
8.0 – Identify and Authenticate Access to System Components
9.0 – (Does not apply)
10.0 – Track and Monitor All Access to Network Resources and Cardholder Data
11.0 – Regularly Test Security Systems and Processes
12.0 – (Does not apply)
Related Articles
Feb 07th, 2024
How Does Kubernetes Work?
Feb 08th, 2023
Future-Proof Telecom Modernization with SUSE ATIP
Feb 01st, 2023
Container Security: Supply Chain Security
Nov 29th, 2022