End-to-End Vulnerability Management for Images, Containers and Kubernetes
NeuVector 3.2 Release Adds a Vulnerability & Compliance ‘Explorer,’ High Performance Scanner, and Host Process Protection
The ‘Shift-Left’ movement to build security into the CI/CD pipeline continues to grow. Vulnerability management is a critical component of this, and organizations must ‘Shift-Left, then Shift-Right‘ in order to fully protect critical assets and sensitive data throughout the entire container lifecycle.
NeuVector helps enterprise DevOps and security teams to achieve automated, end-to-end vulnerability management with a new Vulnerability and Compliance ‘Explorer’ to quickly investigate, prioritize, report, and mitigate potentially damaging vulnerability and compliance issues.
End-to-End Vulnerability Management
The model for end-to-end vulnerability management that NeuVector helps implement follows the Assess, Prioritize, Act, and Improve workflow as shown below.
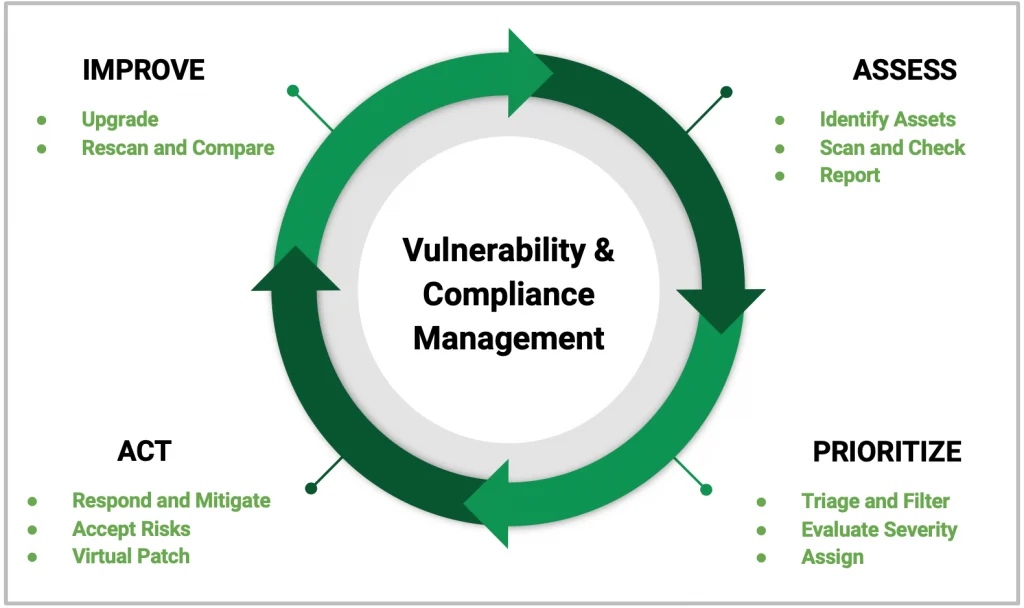
With the new Vulnerability and Compliance ‘Explorer,’ DevOPs and security teams can:
- Easily filter for viewing or downloading of reports, by typing in a search string or using advanced filters next to the box. The advanced filter allows users to filter vulnerabilities by ‘fix available’ (or not available), urgency, workloads, services, namespace, and other criteria.
- Investigate the Impact of vulnerabilities and compliance checks by clicking on the impact row and reviewing affected images, nodes, or even running containers.
- View the Protection State (exploit risk) of any vulnerability or compliance issue to see if there are NeuVector Run-Time security protections (rules) enabled which Virtually Patch impacted nodes or containers.
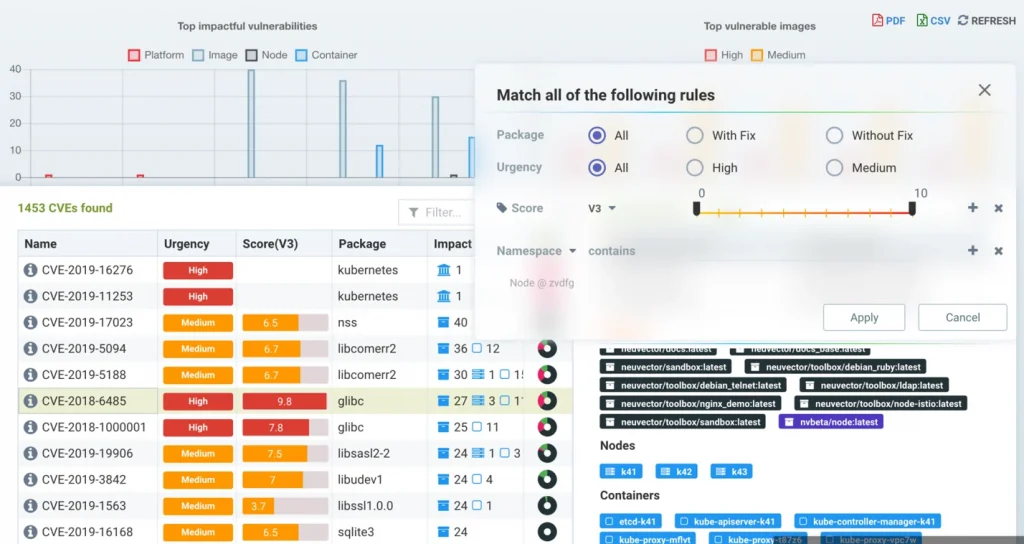
The screenshot above highlights the following powerful capabilities for investigating vulnerabilities or compliance check (CIS benchmark and custom tests) results:
- Sort, filter vulnerabilities by Urgency or other attributes, then investigate the details of a vulnerability by clicking the ‘i’ information button
- Summarize the Impact or each vulnerability in the Impact column – for example the highlighted vulnerability impacts 27 images, 3 nodes (hosts), and 13 containers
- See a graphical summary of the protection status of each vulnerability, with red indicating there are assets (containers, nodes) running in production unprotected by NeuVector, which contain that vulnerability
- Drill down to view the impacted Images, Nodes, and Containers (lower right) to gauge the exploit risk, with color coded indicators to show which assets are protected, or ‘virtually patched,’ by NeuVector, and which are exposed to exploits.
Virtual Patching Protects Production Workloads and Hosts from Vulnerability Exploits
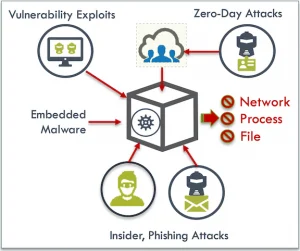 The term Virtual Patching refers to the ability to virtually patch a vulnerability in a running container or host, without having to actual patch or remediate that specific vulnerability in a library or package. In essence it means that the running asset (container, host etc) is protected against an attempted exploit of the vulnerability.
The term Virtual Patching refers to the ability to virtually patch a vulnerability in a running container or host, without having to actual patch or remediate that specific vulnerability in a library or package. In essence it means that the running asset (container, host etc) is protected against an attempted exploit of the vulnerability.
How is this accomplished? With the NeuVector container security platform, all authorized application container behavior such as network connections, processes, and file activity are whitelisted, either through the behavioral learning process or automation through ‘security policy as code.’ Once the workload or host is put into a monitor or protect mode, all vulnerabilities become ‘virtually patched,’ because an attempted exploit will certainly create an unauthorized network connection, process, or file access. These exploit attempts will be detected and alerted (in Monitor mode), and blocked (in Protect mode).
The virtual patching capability in NeuVector gives DevOps teams more time and breathing room to patch critical vulnerabilities. It also gives them the confidence to run containers in production which have vulnerabilities where there is no fix available yet.
Protects Against More Than Vulnerability Exploits
The whitelist based security model includes specifying network connections and ‘Layer7’ application protocols to be allowed, in addition to process and file activity. This means that in addition to virtually patching vulnerabilities, the NeuVector run-time security capabilities protect against embedded malware from starting, zero-day attacks (unknown vulnerabilities), insider and phishing attacks.
High Performance Scanning for Large Registries [tech preview]
NeuVector 3.2 also includes a tech preview of high performance parallel scanners for images in registries. Customers can deploy additional scanners to run in parallel for quickly scanning registries with thousands or tens of thousands of images. This capability extends the market leading scanner performance of NeuVector to handle the scanning requirements of the largest enterprises.
The additional scanners are deployed in a Kubernetes cloud-native way as a deployment, where a replica number specifies the number of scanner containers to be deployed, as shown below.
apiVersion: apps/v1
kind: Deployment
metadata:
name: neuvector-scanner-pod
namespace: neuvector
spec:
strategy:
type: RollingUpdate
rollingUpdate:
maxSurge: 1
maxUnavailable: 0
replicas: 2
selector:
matchLabels:
app: neuvector-scanner-pod
template:
metadata:
labels:
app: neuvector-scanner-pod
spec:
imagePullSecrets:
- name: regsecret
containers:
- name: neuvector-scanner-pod
image: neuvector/scanner
imagePullPolicy: Always
env:
- name: CLUSTER_JOIN_ADDR
value: neuvector-svc-controller.neuvector
restartPolicy: Always
The NeuVector Controller container will schedule image scanning tasks to all available scanners, which can be scaled up or down using standard Kubernetes commands.
NeuVector Strengthens Host Protection in Production
The new release of NeuVector also extends the leading run-time container security platform with enhanced host (node) security. In the same way that NeuVector automatically baselines and whitelists container processes to detect suspicious activity, host processes are now baselined, and hosts (nodes) can be put in the Monitor (alert only) or Protect (block process) mode.
This enhances existing host protections which include detection of privilege escalations and known suspicious process such as reverse shells, port scanning, and tunnels. Hosts are also automatically scanned for vulnerabilities and have the Docker and Kubernetes CIS benchmarks run, including any customized compliance checks.
Full Lifecycle Container Security
It takes a broad spectrum of security and cloud-native features to be able to integrate security into the CI/CD pipeline all the way into production. A layered security approach for defense in depth starts with the beginning, ‘left-side,’ of development with vulnerability and compliance scanning, and proceeds to the right with strong network, container, and host protections. Tying the left to the right is critical to understanding the actual risk of exploit. Vulnerability scanning without virtual patching will overwhelm teams with non-actionable data, and run-time protections without vulnerability and compliance management in the CI/CD pipeline will increase the risk of exploits unnecessarily.
Related Articles
Feb 01st, 2023
Container Security: Network Visibility
Jul 06th, 2022
The Developers Focus, the Team Quickens
Oct 28th, 2022