Safety RAM: Protecting memory section with checksum
This particular blog post is not going to be about Linux memory managements and its safety or how to write a safety critical software but will touch on the topic that all safety critical software must address properly. This topic is Freedom From Interference (FFI). Before we dive in, let’s define some terms and what do they mean in reality:
| ISO26262 | Automotive standard for functional safety | This gives you some guidance what you shall be doing to make safety critical software. At least in automotive. If you are care mainly about software then Part 6 of this standard is the most important. |
| QM | Quality Managed software | Not a safety critical software. It can (and will) go nuts and start writing to your memory or halt the CPU. |
| ASIL A-D | Automotive Software Integrity Level | Safety critical software for automotive. This software can also go nuts. But the probability of this happening is limited. How much limited depends on the integrity level where ASIL D is the highest integrity. |
The Part 6 of ISO26262 defines the freedom from interference as absence of cascading failures between software components. In another words how to ensure that safety critical component runs as designed without giving a chance to others (less critical component) to impact the execution. There are in general 3 types of of interference: spatial (memory), temporal (scheduling) and communication (corruption of input and output data). And as the title suggests here we’ll deal in detail only with one particular hardware independent mechanism of memory protection.
But in general there are several more mechanisms one can think of when it comes to spatial freedom of interference:
- protecting a memory region with a checksum
- protecting each variable by dual storage of its complement
- memory protection mechanisms implemented in operating system, base software or hardware layer
As said, this post is mainly about (1) – protecting a given memory section of a process with checksum. This will be illustrated on an example for Linux operating system but essentially (as you will see later) it is more suitable for more bare-metal applications. In all environments it shall be assumed that any other process with lower ASIL (or QM) than desired integrity level of your component can (and will) execute wrongly and will (if it has a chance) change your memory. Often we cannot stop this from happening but we can at least ensure detecting it in timely manner and take corrective actions.
But without further ado let’s go through the example. All the source code shown here (and more) can be found on GitHub here.
This example has a particular goal of protecting a dedicated memory section of a process with a checksum. This shall allow us to detect any intrusions and reset the process in case the memory corruption happens. There is however one important assumption here: no preemption can happen in the safety critical section of the code and no other code can execute in parallel (single core CPU). This section is represented by this function:
| th_safram_crc.c – Safety critical section |
|
Also please note that the stack (or any other memory section besides “.data_safram” in fact) is not protected. So if this were running on a bare-metal with simple preemptive scheduling then no spatial freedom of interference would be achieved as any other process could alter the memory during execution of safety critical section (e.g. imagine other process changing the memory just after the checksum is checked) and no mechanism would detect that (actually we would even store a new checksum at the end of the run calculated over wrong data and keep going).
But let’s back up a little – the first step is to define the memory section in a linker script . In our example we’ll call this section “.data_safram”:
| data_safram.ld – Linker script – define custom memory section |
|
Note that the “. = . +1” added one byte at the end of this section. This is where we’ll be storing our checksum. This linker script then can be then passed to linker using “-T” option (if using gcc):
| Makefile – Linker option |
|
Note that this way the default linker script is used and only change is a newly added memory section. Then we can start putting variables to this section:
| th_safram_crc.c – Safety critical variables |
|
To check if our memory section is correctly defined, we can run:
| readelf – Memory sections |
|
Linker will supply addresses we can use to know where our “.data_safram” memory section starts and ends. In the code these are following “extern” variables:
| safram_crc.h – Start and end address of the safety RAM |
|
To illustrate, the memory layout of our application looks like as shown on the following figure. This picture is inspired by this.
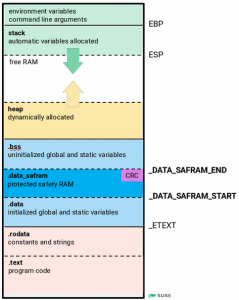
And with all that in place, we can finally implement the functions to store (protect) and check the checksum. The checksum used is the J1850 CRC-8 as described in this AUTOSAR specification of CRC routines.
The CRC approach is fine here as this intended against random faults, not a malicious attacks against our software. For large datasets one may however want to replace CRC-8 by CRC-16 or CRC-32.
| safram_crc.c – Function to protect and check the safety |
|
These can be then used at the beginning and end of our safety critical section – please see above. Then comes a question what to do in case a memory corruption is detected. In simple hardware this would be a reset, in our example we will just restart the process hoping that everything will come back to order:
| th_safram_crc.c – Restart process in Linux |
|
This piece of code is inspired by this answer.
So let’s test all that. For that we will also need a way to corrupt the data. Luckily in Linux this can be done rather easily by altering the “/proc/$pid/mem” with the right privileges:
| th_safram_corruption.c – Accessing other process memory in Linux |
|
This piece of code is heavily inspired by this.
Here you can see the results – the “…” lines are just an attempt to show the time alignment.
| Process 1 – ASIL | Process 2 – QM |
| th_safram_crc | th_safram_corruption |
|
|
You can see that the process 1 is restarted whenever we corrupt the memory from process 2. If you don’t then you might be prevented from writing to the other process memory by the way your Linux distribution is configured. But that’s a topic for the future postings. This example shall however run fine on openSUSE Leap 15.
So it works but to be clear the process 1 here is not ASIL at all. Firstly I have not followed any coding practices required by ISO26262 but even if I did the assumption about preemption is not met here anyways. So please take this as an example that wrong (not suitable) technical concepts do not lead to safe software even if the software is otherwise completely ISO26262 compliant. On top of that we are running on non-safety Linux operating system so our process reset mechanism cannot be relied on and nothing ensures that our checking gets even executed. So no ASIL here nowhere near, sorry.
To sum up this approach comes handy if we need to protect global static variables in between of execution of function runs (e.g. states) and we can ensure that safety critical sections will not be preempted by less safety critical software components. The advantages of this approach is that it is mainly about linker and the other code needs to be altered very little and it also doesn’t need much additional memory or computing power. The disadvantage is that often we want to or must allow the preemption and parallelism. In this case we must use other approaches. Please stay tuned if you wonder about dual-storage of a complement or what protection mechanism are implemented in Linux’s memory management.
And as said, all the code is here: https://github.com/llansky3/safram in the “crc” folder.
Update (2022/04/12): There is now follow up blog post: Safety RAM: Protecting variables with one’s complement. And especially the section “Memory corruption problems” is a direct follow up on this blog post.
Related Articles
May 09th, 2023
Safeguard Your SAP Landscape on Google Cloud Platform
Dec 12th, 2023
No comments yet