Test and Configure Active Security for Containers and Kubernetes on Rancher Desktop via Calico Cloud
SUSE GUEST BLOG AUTHORED BY:
Nigel Douglas, Technical Product Marketing Manager for Partnerships and Alliances, Tigera
An open-source desktop application for Mac, Windows and Linux, Rancher Desktop runs Kubernetes and container management on your desktop. You can choose the version of Kubernetes you want to run. You can build, push, pull, and run container images using either containerd or Moby (dockerd). The container images you build can be run by Kubernetes immediately without the need for a registry.
Installation requirements:
https://docs.rancherdesktop.io/getting-started/installation/

Once installed, users see a simple user interface to configure the CPU and Memory required for their 1-node Kubernetes cluster:
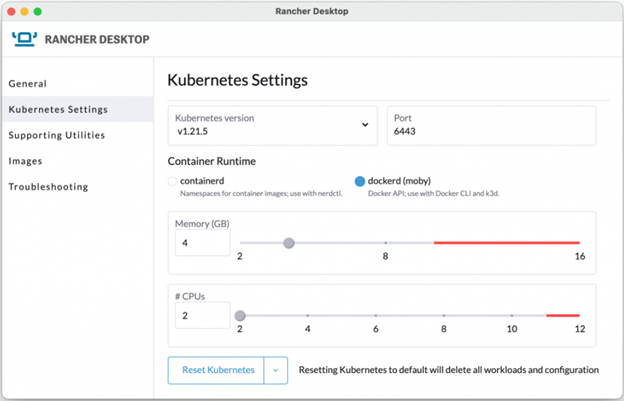
In my case, I would run the Mac (Intel) installer located in the rancherdesktop.io landing page:
https://github.com/rancher-sandbox/rancher-desktop/releases/download/v1.1.1/Rancher.Desktop-1.1.1.x86_64.dmg
1. Choose the version of Kubernetes you wish to test
Project Calico supports the latest stable release of Kubernetes.
I chose ‘containerd’ as the runtime of choice. Moby is also supported.

2. Watch Docker Desktop auto-magically create a 1-node cluster on your desktop
You can monitor the progress of your cluster creation in the bottom right corner of the UI:
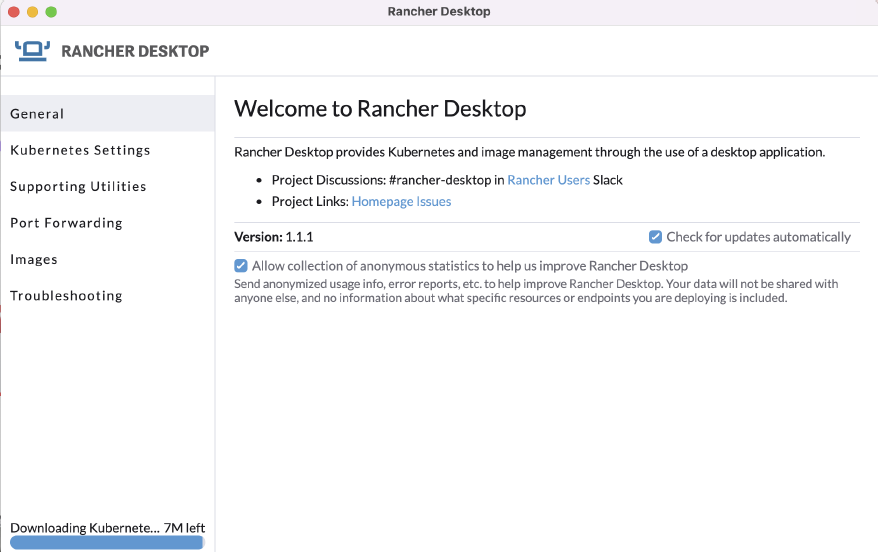
This entire process took little over a minute to create and provision the virtual machine required to power Rancher Desktop:
3. Assign the relevant CPU and memory for your lightweight Kubernetes cluster

4. Open up a local terminal to access your cluster
Confirm your VM is running and in the status ‘READY’: Kubectl get nodes
Confirm your pods are running, and similar in status ‘Running’: Kubectl get pods -A


5. Install Project Calico
Install the Tigera Calico operator and custom resource definitions:
kubectl create -f https://projectcalico.docs.tigera.io/manifests/tigera-operator.yaml
Install Calico by creating the necessary custom resource:
kubectl create -f https://projectcalico.docs.tigera.io/manifests/custom-resources.yaml
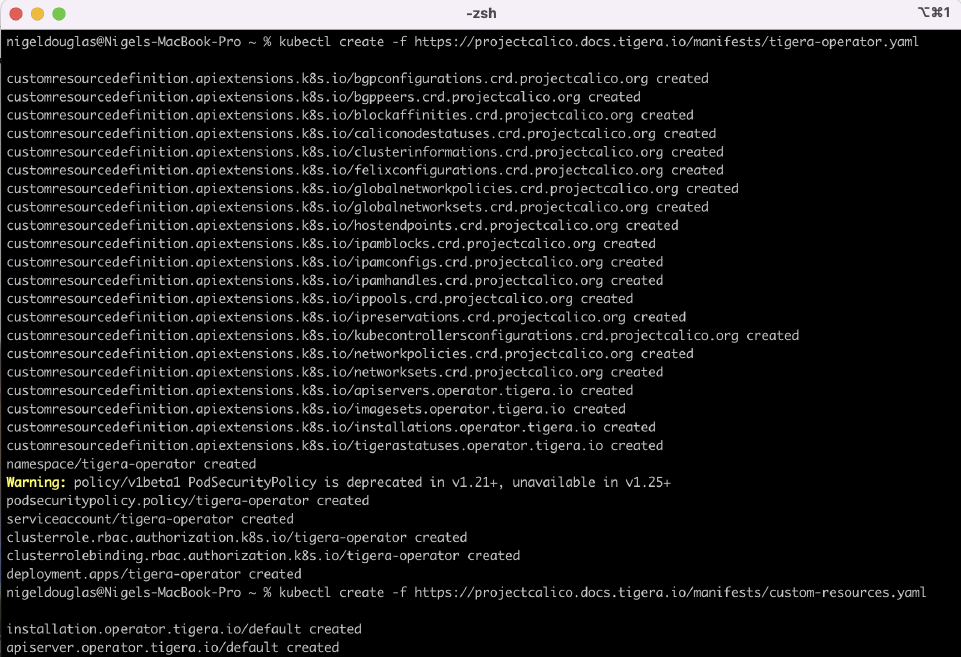
6. Confirm all pods are running
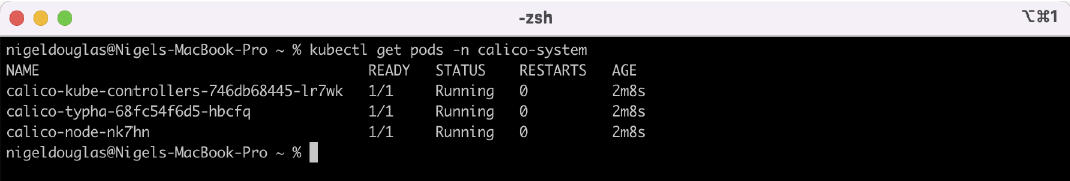
The Calico-node pods running within the network namespace – calico-system:
watch kubectl get pods -n calico-system
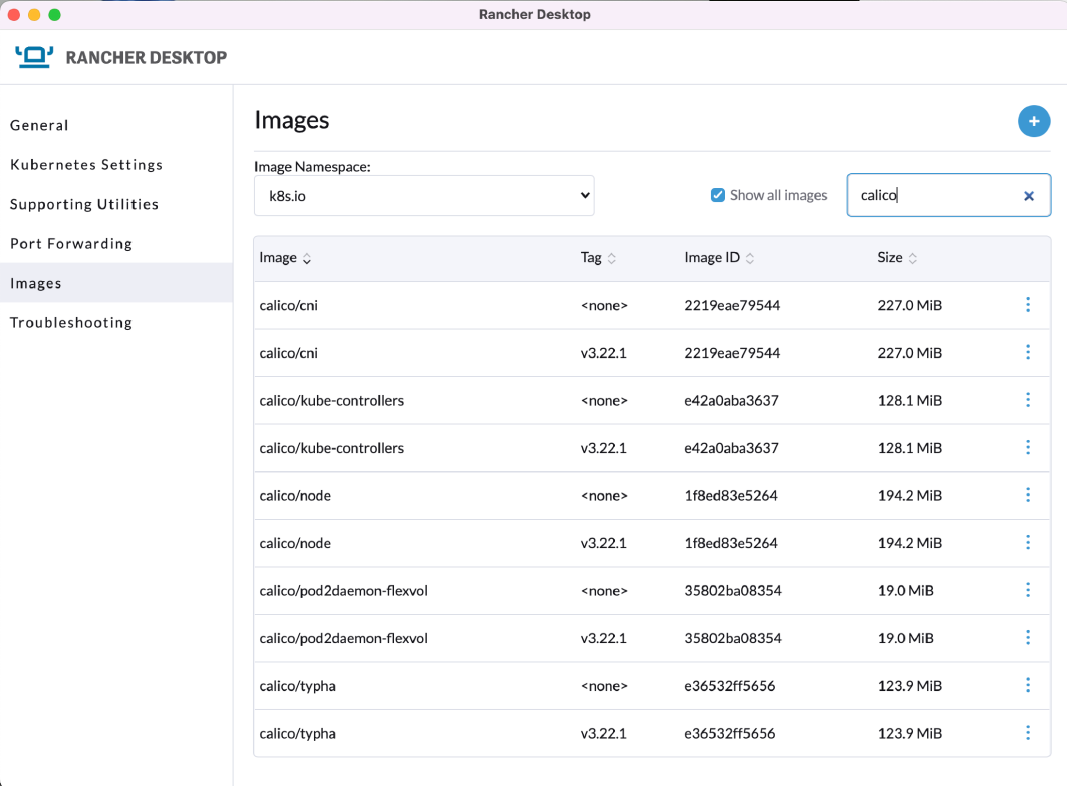
On a side note, you can confirm those images are in the Rancher Desktop UI:
With Rancher Desktop, users can now test and configure best-in-class Security Policy practices via Project Calico in seconds. This speeds up time for testing with limited overhead on platform teams who would otherwise need to allocate resources for testing Kubernetes. SUSE and Tigera expand this partnership by allowing users to connect their Rancher Desktop cluster to Calico Cloud – A Cloud-Native Application Protection Platform (CNAPP) that prevents, detects, troubleshoots, and automatically mitigates risks of security issues for containers and Kubernetes during build, deploy, and runtime.
How does it work?
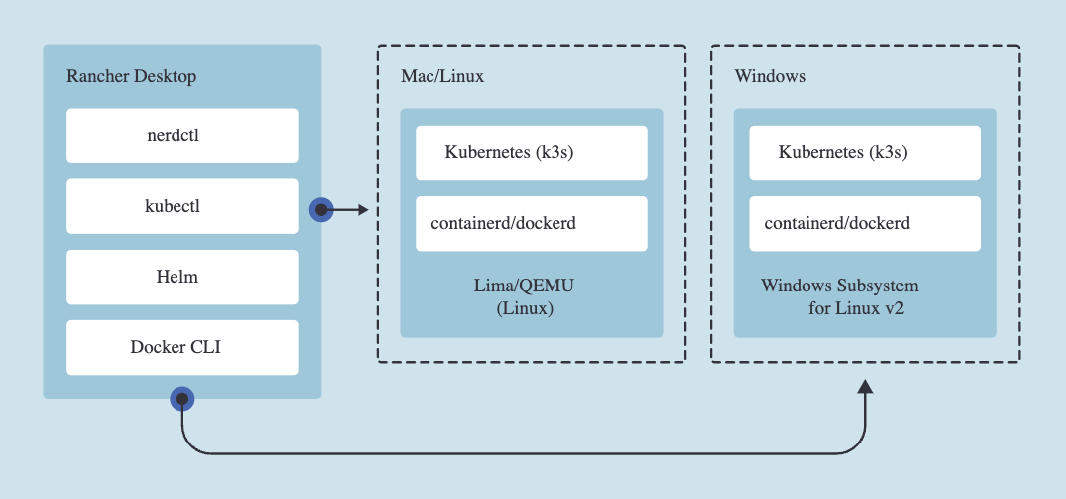
Rancher Desktop is an Electron based application that wraps other tools while itself providing the user experience to create a simple experience. On MacOS and Linux, Rancher Desktop leverages a virtual machine to run containerd or dockerd and Kubernetes. Windows Subsystem for Linux v2 is leveraged for Windows systems. All you need to do is download and run the application.
If there’s an issue with your cluster, Rancher Desktop provides a simple, lightweight Kubernetes Configuration through a simple user interface allowing users to configure how Kubernetes works. This includes:
● Setting the version of Kubernetes you want to use
● Choosing your container runtime
● Configuring the system resources for the virtual machine (on Mac and Linux)
● Resetting Kubernetes and/or the container runtime to default with the push of a button
Calico Cloud protects containers during development and production:
● Reduces attack surface with vulnerability and misconfiguration detection.
● Provides runtime protection from known threats and zero-day vulnerabilities.
Calico Cloud also reduces the attack surface with zero-trust workload access and identity-aware microsegmentation:
● Prevent ransomware, APTs, and DDoS attacks with Calico Cloud workload-level security controls.
Monitor and troubleshoot service performance in real time. In case of a breach or vulnerability, get instant granular information on compromised services and evaluate blast radius through:
● Dynamic Service and Threat Graph
● Performance hotspots
● Dynamic Packet Capture

To learn more about Calico, signup for 14-days free trial of Calico Cloud.
 Nigel is a Technical Product Marketing Manager for Partnerships and Alliances at Tigera. He is responsible for leading Tigera’s content creation for platform partners such as SUSE. Prior to Tigera, Nigel held technical consultancy roles at Software Security firms such as Solarwinds and Malwarebytes In his spare time, Nigel enjoys watching football/soccer, and going kayaking if the weather is good.
Nigel is a Technical Product Marketing Manager for Partnerships and Alliances at Tigera. He is responsible for leading Tigera’s content creation for platform partners such as SUSE. Prior to Tigera, Nigel held technical consultancy roles at Software Security firms such as Solarwinds and Malwarebytes In his spare time, Nigel enjoys watching football/soccer, and going kayaking if the weather is good.
Related Articles
Mar 13th, 2024