SUSE Delivers Carrier-Grade, Commercial Implementation of Project Sylva
New revenue opportunities emerging at the edge for CSPs
The telecommunications industry’s ongoing cloud native evolution is opening up new opportunities, along with new challenges. Communication Service Providers (CSP), being the natural bridge between end users and cloud services, are writing an important page of this cloud technology evolution.
A number of industry use cases have emerged recently, driven by a need to process high volumes of data very close to where they are generated and enabled by the availability of 5G connectivity and cloud computing capabilities at the edge. CSPs, who own and operate thousands of points of presence and the connectivity infrastructure at the edge, are the ideal candidates to address these emerging industry use cases.
The seminal white paper, “Operators Telco Cloud,” authored by Linux Foundation’s Project Sylva team, perfectly summarizes the opportunities for CSPs. It highlights the inevitable merging of cloud and telco technologies and CSPs’ new ability to deploy cloud technologies to accelerate network modernization and unlock new revenue streams.
However, these new industry use cases at the edge have stringent service requirements, requiring CSPs to expand their capabilities. The telco edge platforms need to support ultra-low latency real-time applications, provide the mandated levels of privacy and security to sensitive and personal data, and provide the computing power needed for local processing of data.
Challenges encountered by CSPs and vendors
The origins of CSPs’ current cloud native evolution can be traced back to the European Telecommunications Standards Institute (ETSI) Network Functions Virtualization (NFV) initiatives from 2012. The ETSI recommendations led to the lift and shift of networking functions software being tightly integrated with vendor-specific hardware to running on commercial-off-the-shelf hardware (COTS).
Over the years, the network equipment providers (NEP) and the independent software vendors (ISV) have redesigned networking functions from the ground up using cloud native principles and implemented them as virtual machines and then later as containers. Despite these efforts, the CSP ecosystem has been slow to deploy and commercialize cloud native edge platforms that host Telco Network Functions (NF). Meanwhile, CSPs have been slow to roll out edge platforms that are co-located in their points-of-presence (POP), running cloud native industry applications. Several technological and operational challenges account for the slow pace of the rollout of cloud native platforms.
Fragmentation at the cloud layer
In the absence of a standardized, common cloud layer, many network element managers (NEM) and application vendors built their network functions on a proprietary Cloud as a Service (CaaS) layer, and in some cases even tied to specific physical compute. This practice led to the proliferation of vertically integrated stacks that don’t provide the benefits of disaggregation. Over the years, the fragmentation caused the following operational challenges for CSPs and vendors.
Vendors developing Network Functions face complexities in proving performance and compliance to multiple telco operators that run different CaaS platforms. Figure 1 displays the long sales cycles faced by the vendors:
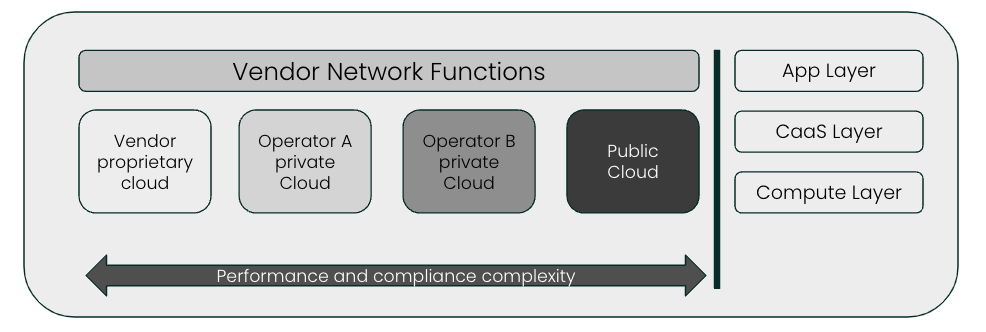
Figure 1: Challenges faced by vendors due to CaaS fragmentation
CSPs deploying vendor Network Functions on vendor-specific cloud stacks face challenges too, from the increased time and effort to perform integration, skillset fragmentation and the increased cost of validation of the “islands” of vertically integrated vendor platforms. Figure 2 describes the fragmentation from the CSP’s point of view.
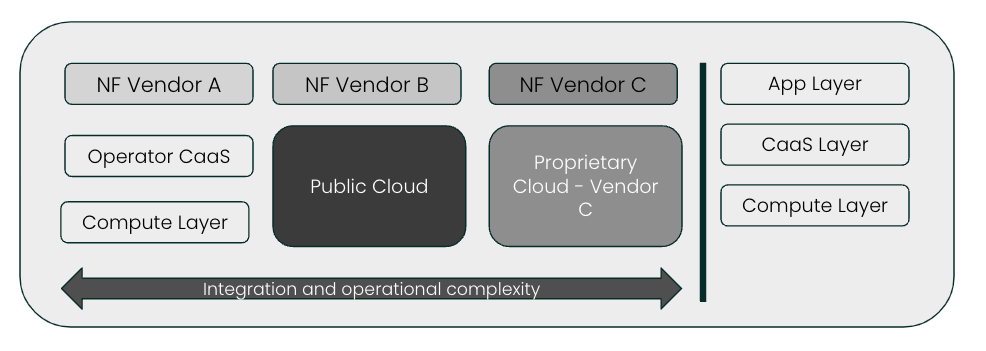
Figure 2: Challenges faced by CSPs due to CaaS fragmentation
In summary, the fragmentation-related challenges faced by CSPs and vendors are additive, resulting in the blunting of innovative ideas, the loss of agility and inefficient consumption of power.
Accelerating the deployment of cloud native edge with Project Sylva
Leading CSPs and NEPs in Europe launched Project Sylva as a Linux Foundation Europe initiative to develop and release a homogenous cloud framework tailored for telco and edge use cases. The goal is to overcome the fragmentation and integration challenges the industry is facing. In addition, Project Sylva aims to develop a reference implementation of the cloud software framework and create a validation program for such implementations.
The goals set forth by Project Sylva benefit all the stakeholders in the ecosystem. A common cloud layer and reference architecture for CaaS will reduce costs for CSPs. A homogenous CaaS layer enables a “build once, deploy many times” model for NEPs and ISVs. Lastly, CaaS providers and system integrators can create a distribution out of Project Sylva, provide support for Project Sylva deployments and provide a validation service.
Since SUSE recognizes the challenges that the telco edge ecosystem faces, SUSE has been a contributing member of Project Sylva from Day 1. SUSE collaborates with Project Sylva partners to develop the CaaS Layer. SUSE’s Sylva compliant edge platform is the Adaptive Telco Infrastructure Platform (ATIP).
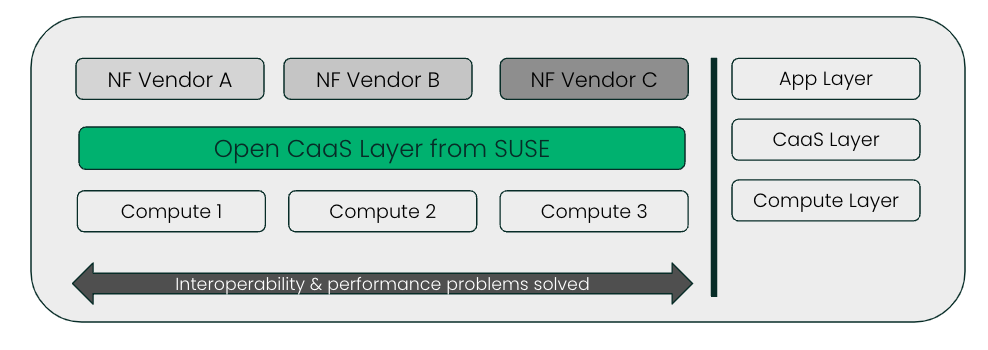
Figure 3: Cloud layer convergence with SUSE
SUSE ATIP acts as the common substrate used by NEMs, ISVs, CSPs and system integrators to develop, integrate and deploy modern, cloud native, telco and industry edge offerings. A few characteristics of the SUSE ATIP platform are worth highlighting:
- SUSE ATIP is an open source platform developed collaboratively with Project Sylva and other community members. SUSE ATIP contains other best-in-class, open source, management, container security, container runtime and OS components.
- All users of SUSE ATIP – NEMs, CSPs, ISVs, community developers and SUSE’s supported customers alike – have access to the same open source distribution and the same bug fixes. The SUSE ATIP distribution is the supported Project Sylva distribution. There are no second-class citizens.
- SUSE ATIP has been purpose-built from the ground up to support telco and edge use cases, which have unique networking performance, security and management-at-scale needs.
SUSE ATIP capabilities that address the edge challenge
Let’s explore the SUSE ATIP solution architecture in greater detail and how its capabilities meet the recommendations proposed by Project Sylva.
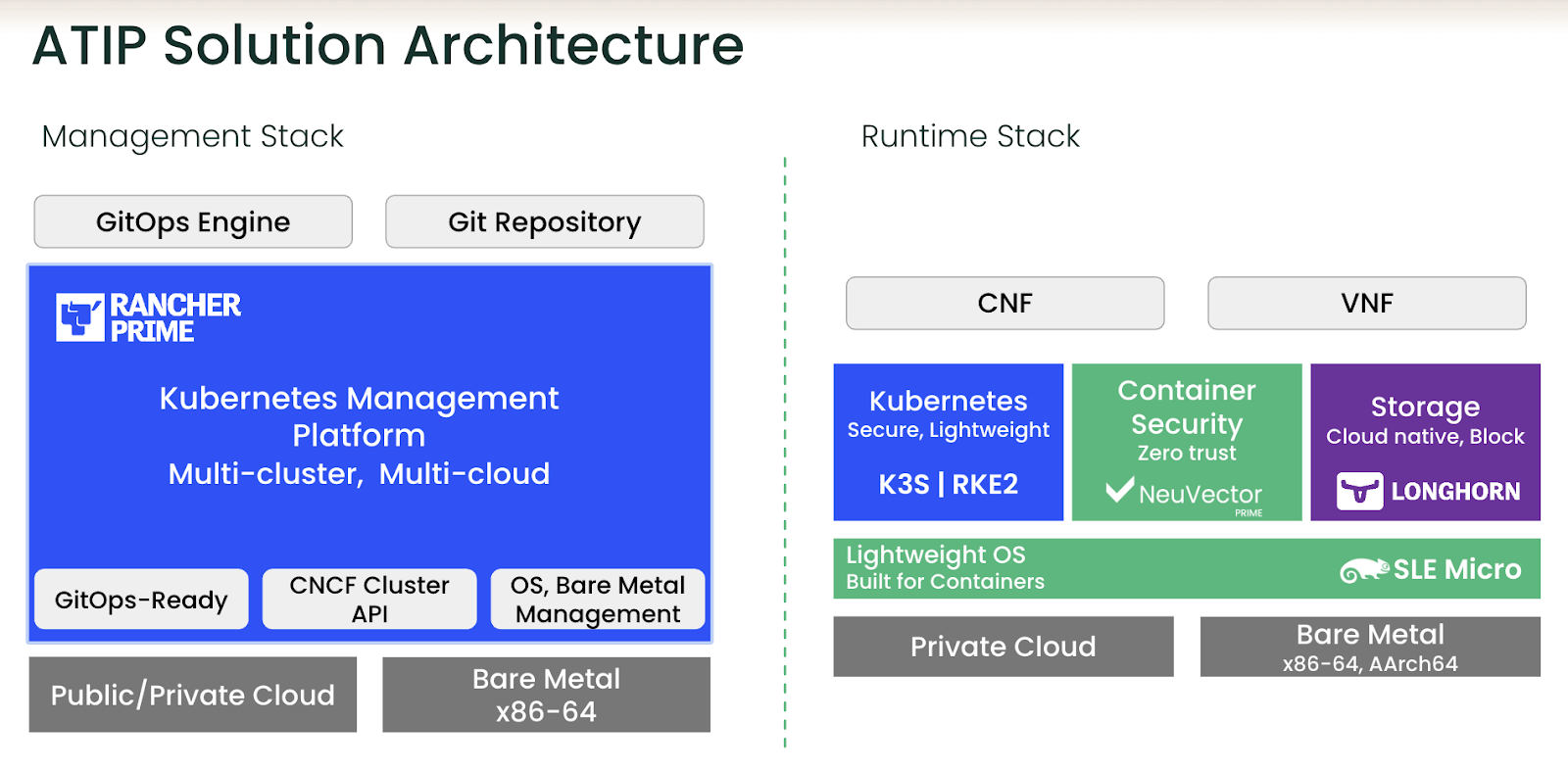
Figure 4: SUSE ATIP Solution Architecture
Project Sylva outlines a broad set of management, performance and security recommendations to satisfy the needs of modern telco and edge applications. SUSE ATIP centers these recommendations, fulfilling them intentionally and with the explicit goal of freeing the telco ecosystem from the challenges it faces today. See how each recommendation is mapped to SUSE ATIP’s functionality below.
| Project Sylva recommendation | SUSE ATIP functionality |
| Declarative approach to manage 1000s of nodes in a distributed cloud, with the ability to automate Kubernetes cluster lifecycle management | At the heart of SUSE ATIP is the Rancher Prime container management system that supports the lifecycle management of Kubernetes clusters at high scale, distributed across multiple clouds and thousands of edge locations. Cluster configuration, tooling, workloads and policies for compliance are defined once in a
template and deployed in 1000s of locations with a “single click”. Rancher Prime’s built-in GitOps engine protects the clusters against drift and loss of compliance. |
| Ability to host most relevant 5G and industry edge applications (e.g. O-RAN, BNG, Video analysis, real-time robot control, AR/VR) | SUSE ATIP’s runtime stack is powered by RKE2, which is based on K3S, the world’s most adopted lightweight Kubernetes distribution. RKE2 is security hardened and certified and optimized for government use and regulated industries. RKE2 supports telco-grade CNI plug-ins such as Calico, Multus and Cilium, allowing it to support line rate bandwidth throughput and encryption/decryption capabilities. SLE Micro is purpose-built to host applications with stringent real-time requirements. |
| Use open source technologies and open APIs to avoid vendor lock-in | Like every other solution offered by SUSE for the last 30 years, SUSE ATIP is fully built on open source technologies. It has a modular and composable architecture. The built-in Edge Image Builder tool lets users pick the right open source components for SUSE ATIP that suit their needs, including the ability to choose from a range of plug-ins for specific storage or network performance needs and build images that are customized to the users needs from first boot. |
| Provide best in class energy optimization to cope with high level of distribution | Both RKE2 and SLE Micro, the OS that is packaged with SUSE ATIP, are lightweight distributions that are purpose-built to run in compute, storage and memory constrained environments. RKE2 and SLE Micro only contain packages that are needed for edge environments and don’t include any packages that are only needed in enterprise or data center environments, thereby reducing or eliminating the need for large servers at the edge that are energy-inefficient. |
| Adhere to EU security recommendations pertaining to data security and sovereignty, and the ability to detect and prevent attack scenarios. | Every product in the SUSE ATIP platform is designed to meet or exceed the most stringent security regulations of the EU. The small footprint of RKE2 and SLE Micro minimizes attack surfaces. SLE Micro is also immutable, preventing bad actors from modifying the filesystems. Every transactional update is accompanied by security hardening tests, and the updates are rolled back if security checks fail. NeuVector Prime, SUSE’s full lifecycle, cloud native container security solution, is available as an optional package with every SUSE ATIP distribution. NeuVector Prime performs vulnerability scanning prior to onboarding images and enforces runtime policies on intra-cluster traffic. |
SUSE recognizes that not all CSPs and Service Providers have the needed skills to deploy and manage the open source SUSE ATIP distribution, at high scale and in compliance with government and security regulations. SUSE offers four levels of services to such customers to ensure their success in transitioning to cloud native.
- Edge Ready Design: SUSE collaborates with the customer to design the solution with a plan for implementation
- Edge Ready Implement: SUSE collaborates with the customer and builds an MVP for testing and validation
- Edge Ready Scale: SUSE provides deployment at scale
- Edge Ready Support: SUSE provides sustained support for the Edge stack, including bug fixes and patches
Reach out to SUSE to explore how we can help you implement the edge solutions that work best for your cloud migration journey.
Learn more:
- Vision for Telecom at the Edge – White Paper
- SUSE Telecom Industry Solutions
- SUSE Edge Solutions
- Parallel Wireless and SUSE Partner to Deliver Hardware Agnostic Kubernetes-Enabled Solutions
Related Articles
Feb 27th, 2024
What is Public Cloud Computing and How Does It Work?
Apr 26th, 2024
What’s New in SUSE ATIP 3.0?
Jul 03rd, 2024
Ensuring Business Continuity Post-CentOS EOL
May 09th, 2023