End-to-end Encryption for Your Rancher Cluster with Linkerd
SUSE One Partner, Buoyant, has offerings live in the SUSE Rancher Apps and Marketplace and we’ve invited Bouyant to author a guest blog so you can learn more about leveraging the Linkerd service mesh with SUSE Rancher. Originally create by Bouyant, Linkerd is one of only 16 projects carrying the CNCF’s Graduated project status. Bouyant also provides a Linkerd extension to connect to the Buoyant cloud service. Cool stuff. ~Bret
SUSE GUEST BLOG AUTHORED BY:
Alejandro Pedraza, Linkerd maintainer and Senior Software Engineer at Buoyant, the creator of Linkerd
Deployment of Linkerd, a CNCF Graduated project, has never been easier
Getting real end-to-end encryption of sensitive customer data on your SUSE Rancher cluster sounds like a complicated challenge—but it’s actually pretty easy with Linkerd, a CNCF member project since 2017.
Linkerd can easily add mutual TLS (mTLS) to any SUSE Rancher cluster, giving you zero-trust security for all data in transit.
But before we dive into the how, let’s explore the what and the why.
What is a service mesh?
A service mesh is a tool that adds observability, security, and reliability features to applications without any code change. It does that by inserting these features at the platform layer rather than the application layer.
A service mesh is typically implemented by deploying network proxies next to app code—a pattern referred to as a “sidecar” proxy. These proxies handle the communication between the services and are the point at which the service mesh features can be introduced. Together, the proxies comprise the service mesh’s data plane, which is controlled by its control plane.

What is Linkerd?
Linkerd pioneered the service mesh category and is the only graduated project service mesh from the CNCF. In a space notorious for complexity, Linkerd takes a human-centric approach: it’s 100% open source, installs in minutes, requires zero configuration, Linkerd can monitor and report per-service success rates and latencies, automatically retry failed requests, and encrypt and validate connections between services.

Most importantly, for our purposes, Linkerd can immediately give you mTLS encryption and authentication for your sensitive data, without the pain of setting up your own PKI infrastructure.
Why Linkerd?
Zero-trust traffic security: Linkerd adds mutual TLS (mTLS), fine-grained identity, and L7 traffic policies, enforcing them all at the level of individual pods and extending naturally to multi-cluster communication.
Avoid C++ vulnerabilities: Linkerd’s Rust-based data plane features native code speed and performance without the memory vulnerabilities endemic to C/C++ proxies.
All the mesh without all the cost: Linkerd’s unique micro-proxy approach means it is orders of magnitude faster and lighter than Envoy-based service meshes.
A graduated CNCF project: Linkerd is a graduated CNCF project alongside other cloud native building blocks such as Kubernetes, Prometheus, and Helm.
How it works
Ready to mesh your Rancher clusters? Let’s do it!
Go to Rancher’s Apps and Marketplace and search for Linkerd.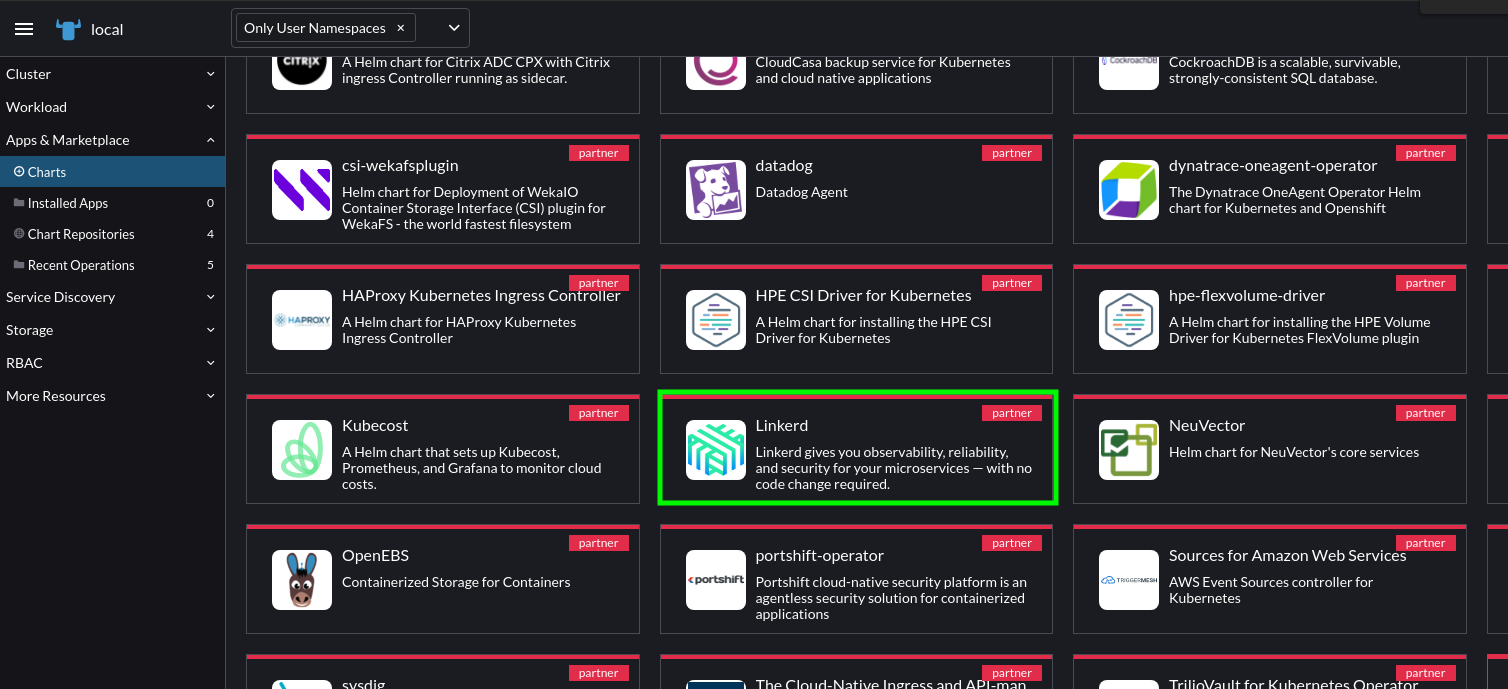
When clicking on Linkerd, you’ll see the Helm chart’s read me with all the config options.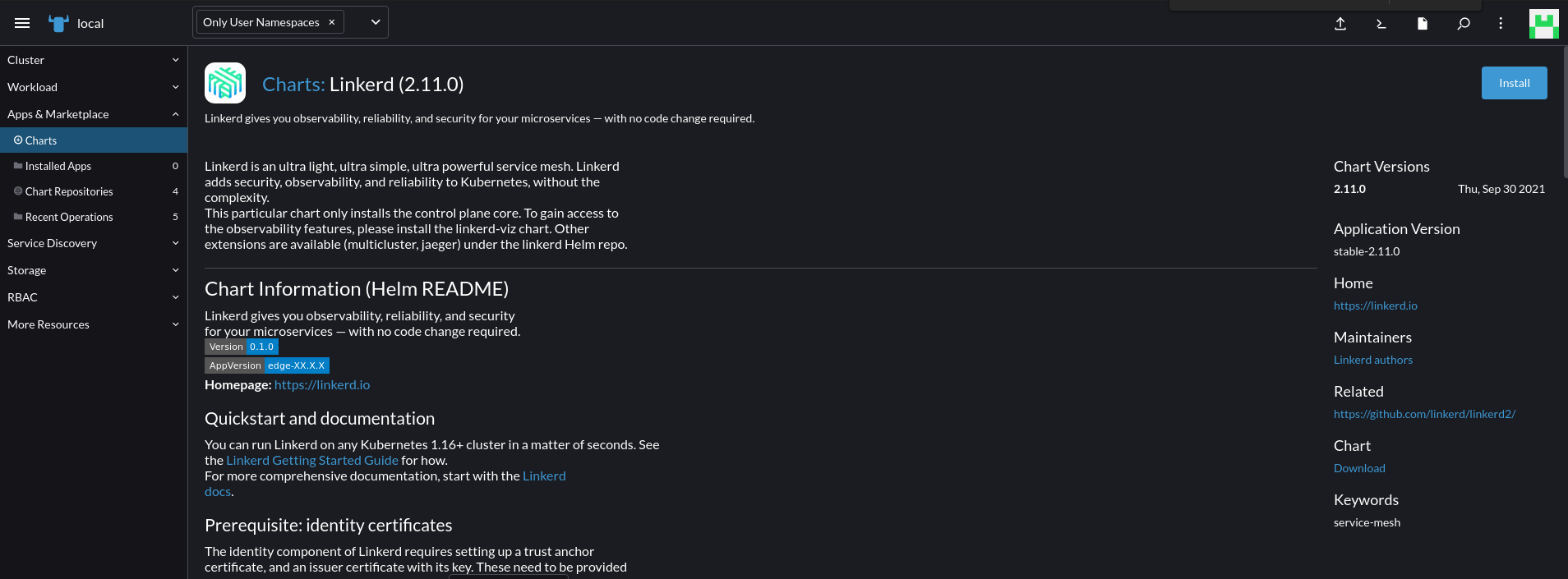
Click on “install” and add the namespace where you want to install Linkerd.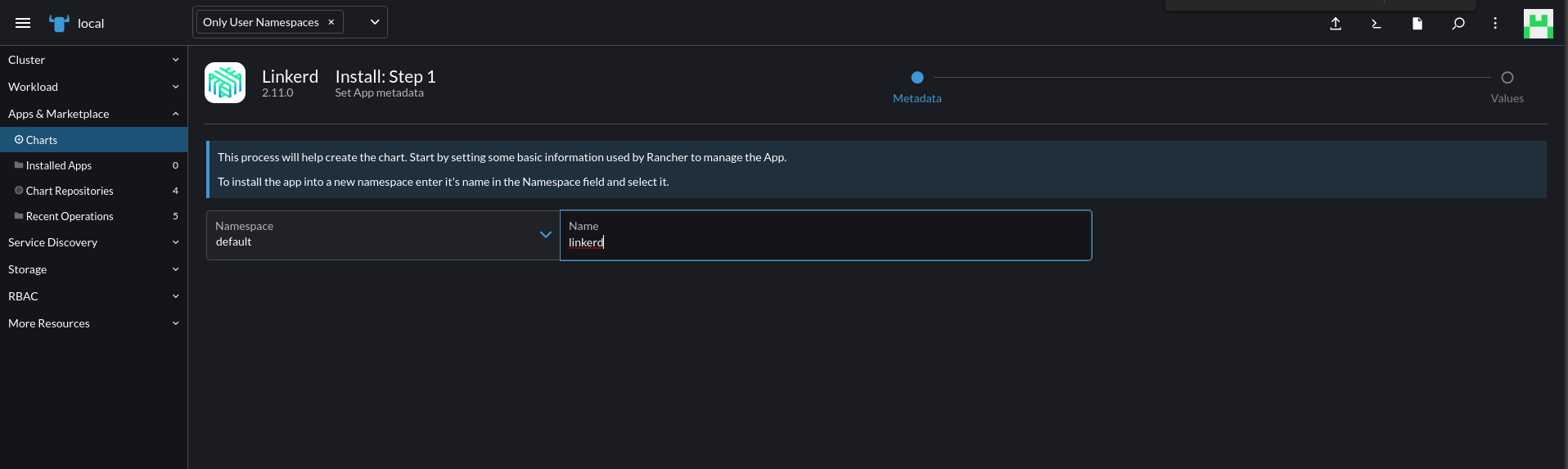
Finally, enter the trust root and the certificate issuer information (you can check the Linekerd reference docs for a quick walkthrough on how to generate these). That’s the minimal config to get Linkerd core up and running, but you can also configure more in the “Edit YAML” tab. Today, we are just installing the default core Linkerd, so go ahead and click “install”. And you’re done—congrats!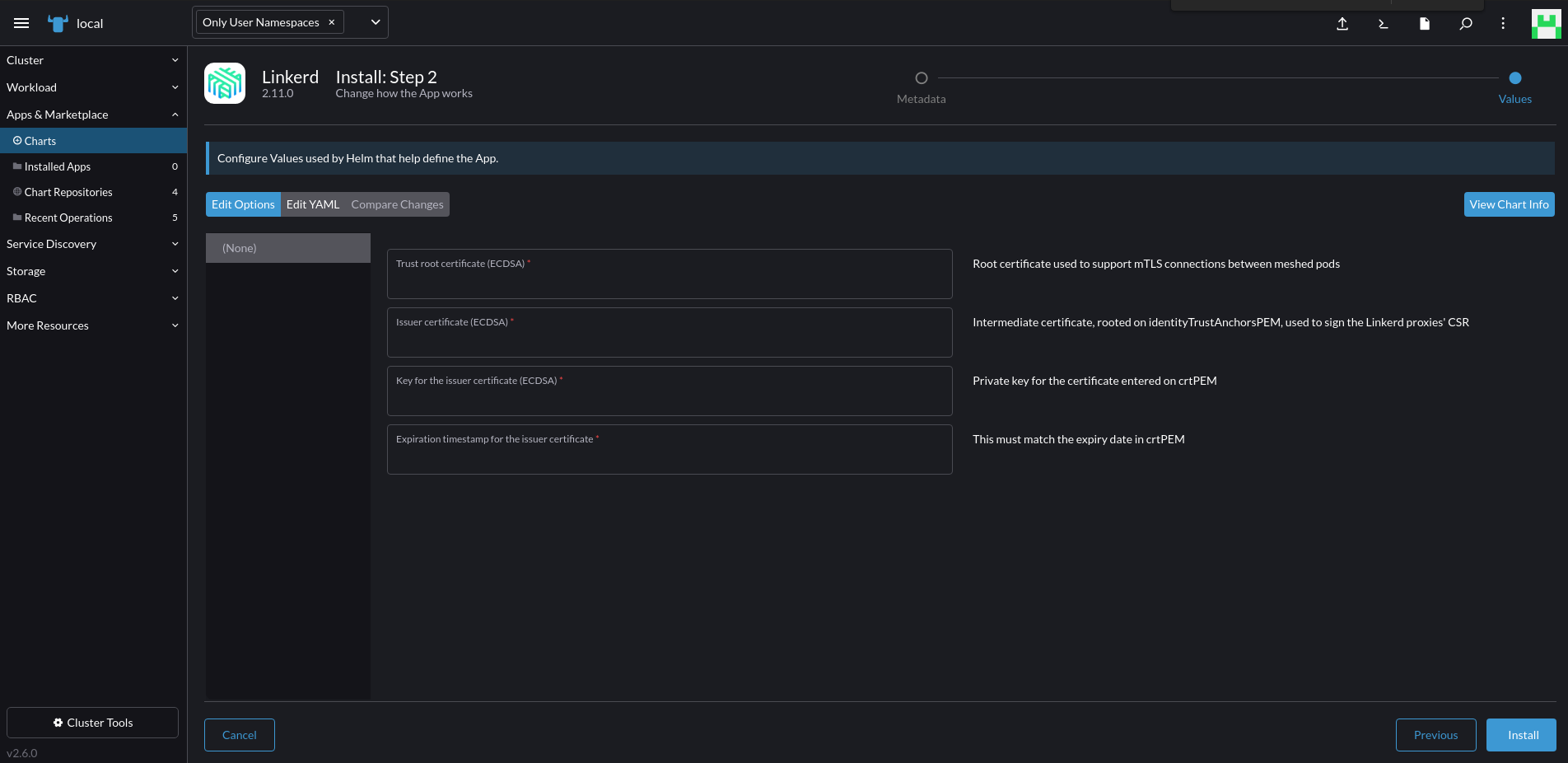
Now that Linkerd is up and running, TCP traffic between all meshed services will be automatically mTLSed, and you’ll benefit from Linkerd’s host of other features, including the recently released policy feature that enables users to control which services connect and send requests to each other.
How do I see the state of my mTLS?
Congrats, you now have mTLS! But how do you tell which traffic is mTLS’d and which isn’t? Enter Buoyant Cloud, a free dashboard for Linkerd by Buoyant, the creators of Linkerd. By connecting your Linkerd-enabled cluster to Buoyant Cloud, you can easily get a breakdown of all traffic flowing through your mesh by TLS status. You can even send an alert when a new type of traffic is detected in your mesh!
Connect your cluster by signing up for Buoyant Cloud and following the simple instructions. Then click on the TLS tab and you should see something like this: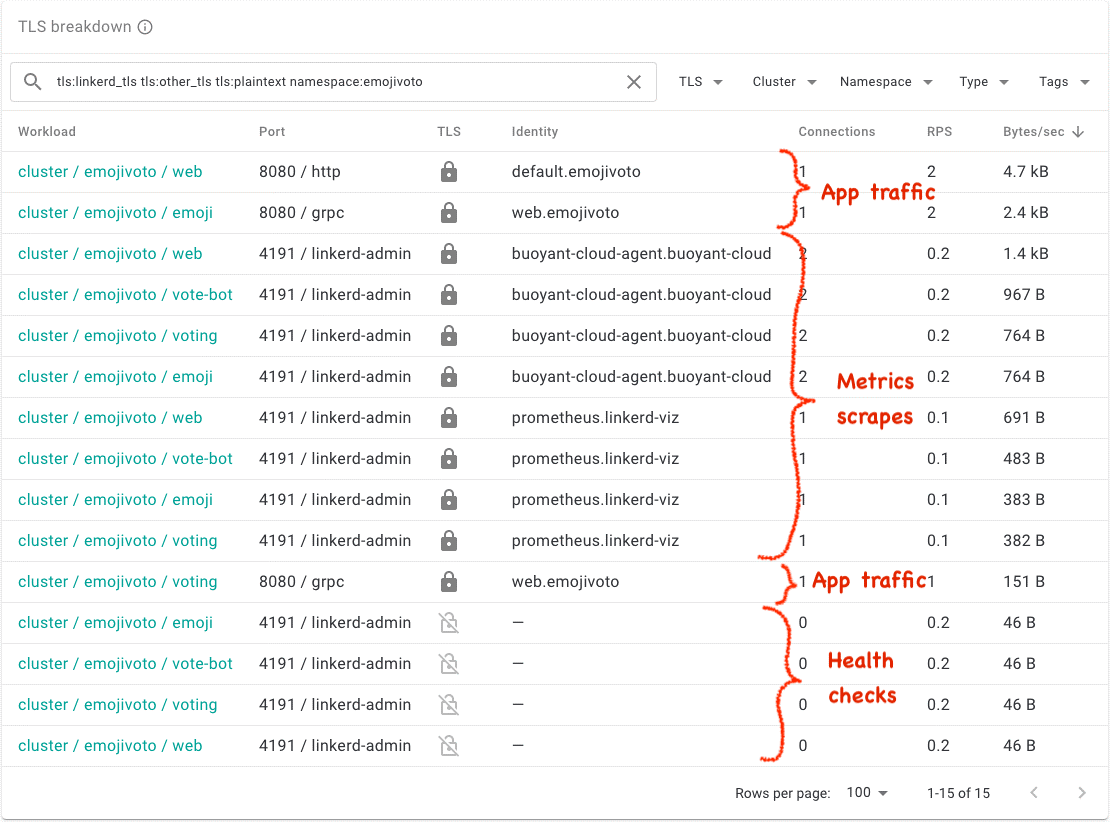
Now you can rapidly identify the different types of traffic on your cluster, including mTLS application traffic, metrics scrapes, and plaintext Kubernetes health checks! With Linkerd applying mTLS and Buoyant Cloud giving you visibility, you’ll always understand the state of traffic on your SUSE Rancher cluster.
Learn more
To learn more about Linkerd and SUSE Rancher, contact the Linkerd team or contact your SUSE Rancher sales representative.
Linkerd is a community project and is hosted by the Cloud Native Computing Foundation. Linkerd is committed to open governance. If you have feature requests, questions, or comments, we’d love to have you join our rapidly-growing community! Linkerd is hosted on GitHub and available in Rancher as well, and we have a thriving community on Slack, Twitter, and the mailing lists. Come and join the fun!
Related Articles
Dec 14th, 2023
saptune 3.1.1 – Do I Need to Update?
Mar 05th, 2024
Connecting Industrial IoT devices at the Edge
Oct 25th, 2023