How to Use NeuVector with the Mitre Att&ck Framework
There are many attack vectors for cloud-native Kubernetes and container deployments, some new and some traditional. To help organizations learn about these and protect against them, MITRE has published a knowledge base of techniques and tactics in a new matrix focused on containers.
The newly published ATT&CK® for Containers provides container-specific attack vectors across the lifecycle of containers, primarily focused on the run-time, or production environment (as opposed to the build CI/CD pipeline) and the host, orchestrator and container attack surface.
The attacks listed can be protected against by the NeuVector Container Security platform, as summarized in the picture below. For each attack, MITRE lists the techniques, examples, and mitigation strategies. We have mapped the NeuVector mitigations to these attacks.
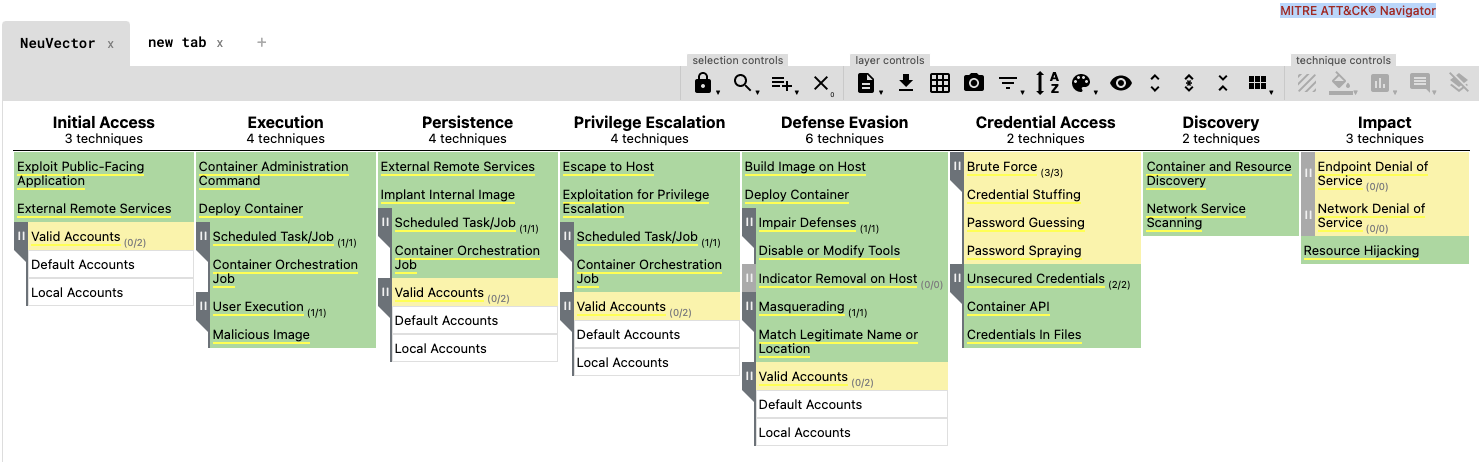
The MITRE ATT&CK® Navigator is an interactive tool which can be found online here in order to examine each attack technique. To load the NeuVector protections into the MITRE ATT&CK Navigator, you can load from this url. In the interactive version, mouseover an attack to see it’s reference and the NeuVector protects. Right click on any attack to see the full description, sample attacks, and mitigations strategies.
The most critical attacks on containers and their infrastructure will come from zero-day attacks where hackers use techniques to exploit unknown vulnerabilities, or gain access and expand the attack using techniques which can’t be detected by traditional security tools. Here are several run-time attack techniques which can be used to start, expand, or execute an attack.
- Deploy Container.
- Exploit Public Facing Applications.
- Privilege Escalations.
- Network Service Scanning.
- Denial of Service / Resource Hijacking.
The NeuVector Container Security Platform is well-positioned to detect and prevent these types of attacks.
Although the matrix is a good container-focused summary, the techniques in ATT&CK for Containers do not include some of the most critical run-time attacks that are possible on containers. For a look at these, we have to look at the other attack matrices for Linux and Network, and there is a high degree of overlap between these matrices.
It is important to address as many of these as possible to provide the broadest detection of events in a typical “kill-chain” of an attack. Attacks usually include network, host (OS), orchestrator, application (container process and file activity), and data storage actions, with the network being the most critical for cloud attacks.
ATT&CK for LINUX
From the ATT&CK for LINUX matrix the following additional categories should be included in container defense strategies in order to protect against run-time attacks.

As can be seen above, NeuVector provides broad coverage for these critical run-time attacks on linux systems. For a full interactive view of the NeuVector coverage for linux, use this link to load it into the navigator tool.
ATT&CK for NETWORK
NeuVector provides broad, unique network protections for container based environments. The NeuVector coverage for ATT&CK for NETWORK is shown below:
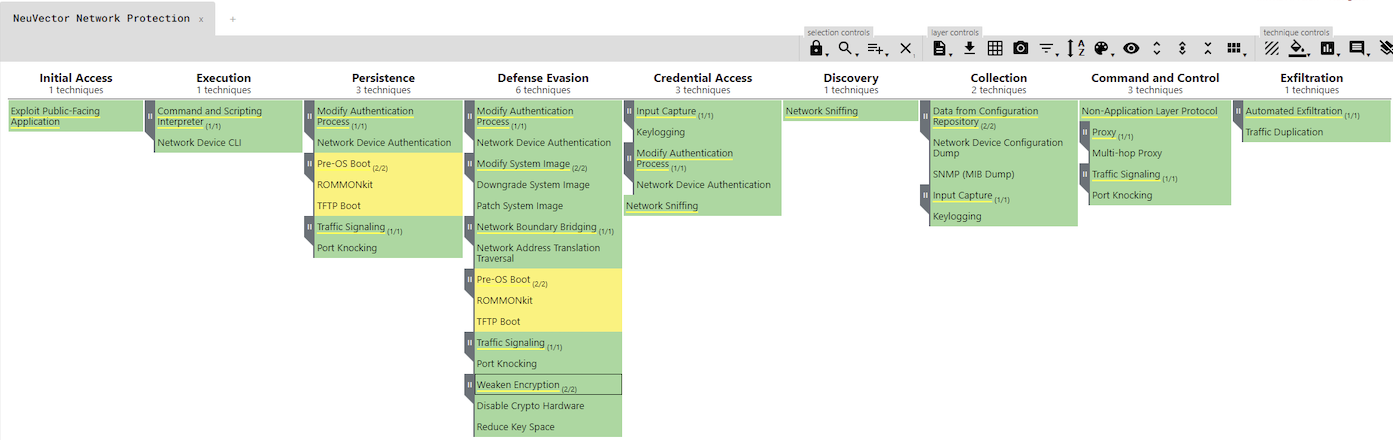
You can view the NeuVector coverage interactively by importing this link into the navigator tool.
The following four categories are especially important in planning defensive strategies for container environments.
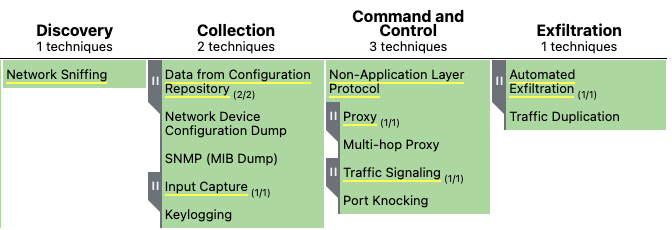
NeuVector is able to protect against these additional techniques by employing a zero-trust security model which prevents unauthorized behavior.
- Discovery. Network Sniffing either through passive monitoring or using Man In Middle (MiTM) attacks.
- Lateral Movement. Can be used to expand the attack and probe for the next step in the “kill-chain.”
- Collection. Data collected to expand the attack or steal sensitive data.
- Command and Control. Typical step in the ‘kill-chain’ to install malicious code or steal data.
- Exfiltration. Stealing of sensitive data will use external network connections.
Employing a Zero-Trust Security Model to Prevent Container & Kubernetes Attacks
Enterprises are moving from a signature-based, deny-list approach to security to a zero-trust security model. In a zero-trust model, allowed behavior is declared, and everything else is deemed untrusted or suspicious.
NeuVector provides comprehensive security for container and Kubernetes deployments by automating security in the entire application lifecycle. In this way, the techniques used by attackers as summarized in the Mitre ATT&CK matrices can be detected and prevented before doing damage.
Summary of Attack Mitigations by NeuVector
- Zero-trust security model.
- Network segmentation (Layer7).
- Network threat prevention including OWASP.
- Process, File and Network security.
- Host protections.
- DLP deep packet inspection.
- Admission Controls.
- Egress Controls for Exfiltration prevention.
- Vulnerability and Compliance Image Scanning.
Related Articles
Jun 20th, 2024