Bringing AI-Assisted Operations to Real Linux Environments with SUSE Multi-Linux Manager MCP Server
AI assistants are impressive in demonstrations, but far harder to apply to real, already running enterprise Linux environments. AI-assisted operation was a promise reserved for single-vendor, new ‘greenfield’ deployments.
Modern data centers are heterogeneous by default, mixing Linux distributions and versions. SUSE Linux, Ubuntu, RHEL and Enterprise Linux clones, and legacy versions running mission-critical workloads coexist in enterprise IT environments. Bridging the gap between Large Language Models (LLMs) and this diverse, real-world infrastructure has been the missing link for AI-assisted operations.
With the tech preview release of the SUSE Multi-Linux Manager MCP server v0.5, now available directly from the official SUSE Registry, SUSE takes a concrete step to close that gap. By moving to registry.suse.com, we are providing the security, trust and tooling in the software supply chain necessary to introduce AI-driven operations (AIOps) to the enterprise.
Importantly, this approach does not require the replacement of existing systems, it enables modernization without disrupting the environments organizations already run.
This is the first time an LLM can safely interact with an existing heterogeneous Linux fleet through a trusted enterprise management platform. It is a foundational step toward making AI a practical operations tool for real-world Linux environments.
It is also a concrete example of how SUSE helps organizations simplify and optimize Linux operations across complex, multi-distribution estates.
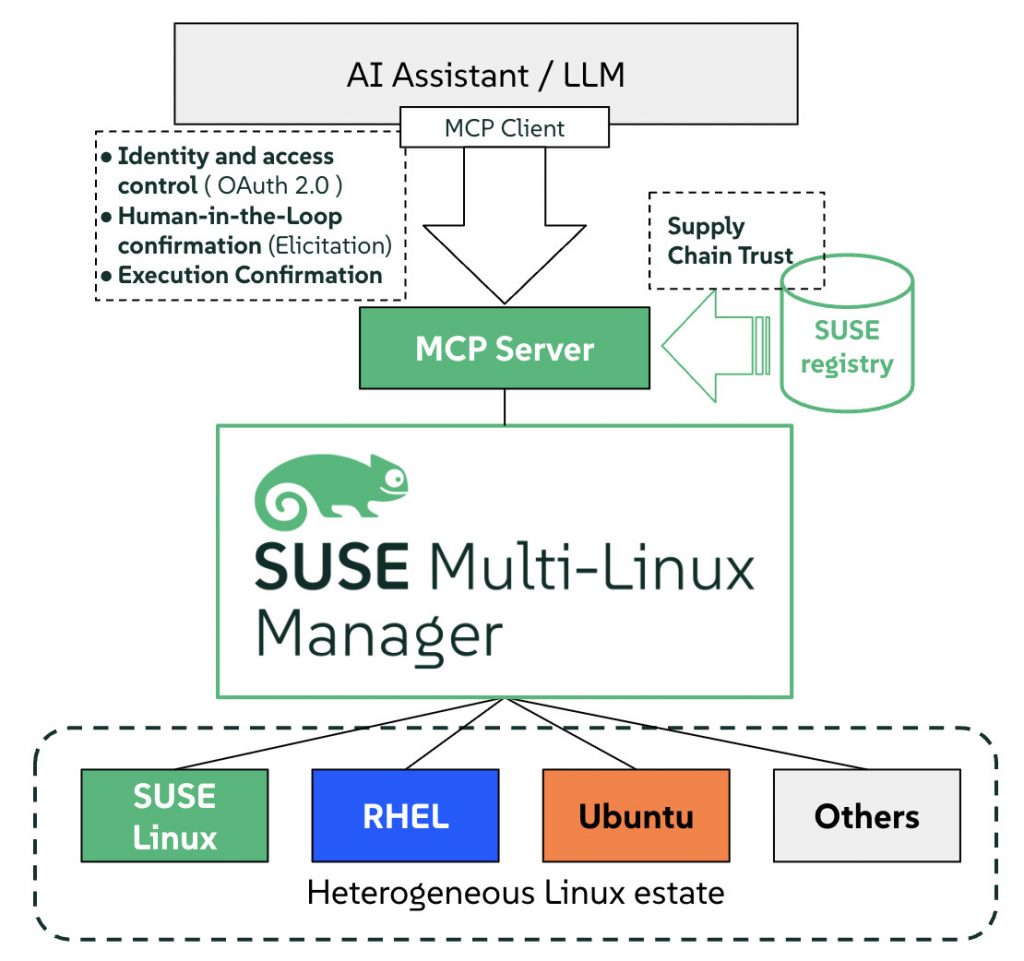
Architecture of AI-assisted Linux operations using the SUSE Multi-Linux Manager MCP Server, with OAuth 2.0 authentication, human-in-the-loop confirmation via elicitation, and trusted supply chain delivery from the SUSE Registry across heterogeneous Linux estates.
Why the SUSE registry matters for AI-assisted operations
Publishing the MCP server at registry.suse.com is not just about convenience. For AI agents to operate infrastructure, trust in the software supply chain is foundational:
- Trusted Provenance & Signing: Every image is signed by SUSE, ensuring the code you run is authentic and untampered.
- Continuous Vulnerability Scanning: Our automated pipelines monitor the container for CVEs, ensuring the management layer remains as secure as the infrastructure it controls.
- Compliance & SLSA Alignment: We are meeting the high-level supply-chain standards that enterprise security teams require for production-ready tools.
Remote authentication: Security for the networked enterprise
Allowing an AI agent to operate infrastructure remotely without strong authentication would be unacceptable in an enterprise environment. This is why v0.5 introduces OAuth 2.0 support.
Previously, AI interactions were largely confined to local sessions. By supporting OAuth 2.0, the MCP server can now operate in secure, remote environments. This ensures that when an AI agent acts on your behalf, like auditing a system or scheduling a patch, it does so within a governed, authenticated framework, enabling a “Human in the Loop” security model.
Enabling human-in-the-loop governance with elicitation
Allowing an AI agent to move from reading data to taking action requires a framework built on trust and transparency. Any system change must be explicitly signaled before it is executed.
By implementing a key feature of the Model Context Protocol known as elicitation, the SUSE Multi-Linux Manager MCP server provides the foundation for confirmation workflows. This allows the server to signal when an action, such as rebooting, scheduling a patch or onboarding a system, requires additional input or approval. This applies not only to configuration or file changes, but also to actions that alter the operational state of systems and can directly impact business continuity.
While the actual enforcement of the human gate is managed by the MCP host or client, our server provides the critical signaling necessary to support a robust human-in-the-loop governance model.
Elicitation enables:
- Human-in-the-loop workflows. The MCP server can signal that confirmation is required before executing changes.
- Governance to be maintained. No high-impact change happens autonomously when clients implement confirmation workflows.
- Risk to be mitigated. Mission-critical environments are protected from unintended AI actions when these signals are respected.
- Resiliency to be prioritized. IT teams remain the final authority, using AI to empower decisions rather than bypassing them.
New tools for agentic management
AI assistance becomes meaningful only when the agent can perform real operational actions.
While the previous versions of the MCP server already provides a wide array of foundational tools ranging from system inventory to user management, version v0.5 introduces several proactive capabilities that significantly expand the agent’s “toolkit”:
- System Bootstrapping (
add_system): You can now use natural language to register and onboard new systems into your management infrastructure across diverse Linux environments. - Proactive Patch Auditing (
get_unscheduled_errata): Instead of reactive monitoring, you can ask the AI: “Identify any critical security patches available but not yet scheduled for my Ubuntu fleet.” The agent identifies the gaps before they become vulnerabilities. - Management of System Groups (
list_system_groups): List existing system groups or create new ones. Add or remove systems to or from system groups respectively.
Note: These are just a few examples of the latest additions. You can find the complete list of available tools and resources in the project documentation.
Expanding the Multi-Linux mission
This is where SUSE’s Multi-Linux mission becomes critical. AI assistance tied to a single Linux distribution has limited value in real enterprise environments. This update enhances our ability to handle updates and CVE audits across a variety of systems, including Ubuntu and Enterprise Linux (RHEL/CentOS) clones.
Looking ahead
As a Tech Preview, v0.5 represents an important milestone toward infrastructure management that is conversational, automated and secure across heterogeneous Linux estates.
You can explore the container image today in the SUSE Registry at registry.suse.com/suse/agentic/mcp/multi-linux-manager:latest . Review the full technical details in the changelog.
To learn more about the Model Context Protocol (MCP) standard and the broader ecosystem for agentic AI, visit the Agentic AI Foundation (AAIF), a part of the Linux Foundation.
For more context on why AI-assisted operations require trusted multi-Linux management and human-in-the-loop governance, read the companion thought leadership article here.
Related Articles
Dec 16th, 2025