SUSE Academic Training Programme
Empowering Universities with SUSE Academic Training Programme
Universities play a vital role in shaping the future of IT professionals. However, the ever-evolving landscape of enterprise open source technology makes it difficult to keep up the pace.
At SUSE, we want to help. We realize it’s crucial to equip students with the skills and knowledge needed to thrive in the industry. Our Academic Training Programme bridges the gap between academia and real-world IT demands by providing comprehensive training on SUSE Enterprise open source products.
to thrive in the industry. Our Academic Training Programme bridges the gap between academia and real-world IT demands by providing comprehensive training on SUSE Enterprise open source products.
Ideal for Universities seeking to enrich their IT curriculum, the SUSE Academic Training Programme provides their students with cutting-edge enterprise open source training opportunities.
We are excited to extend an exclusive invitation to Universities worldwide, offering them the chance to partner with us and integrate our enterprise open source training into their IT courses—for free!
What We Offer:
Free Enterprise Open Source Training: Participating universities have the opportunity to incorporate our Enterprise Open Source Product Training into their curriculum. We offer administration courses such as SUSE Linux Enterprise Server 15 Administration, Kubernetes Administration, and Rancher Manager 2.7 for Rancher Prime Operations. Universities can integrate these courses, including the technical labs, into their IT courses over the desired duration.
Discounted Certification Exams and eLearning Subscriptions: In addition to free training, we’re pleased to offer students a discount on Certification Exams and our eLearning Subscriptions (Silver and Gold) enabling them to continue their education and pursue certification.
Programme Details:
All universities worldwide teaching IT courses are eligible to participate, provided they integrate our training into their curriculum.
Global Reach: The SUSE Academic Training Programme is a global initiative, accessible to universities across the globe.
For further information please reach out to training@suse.com
An Enterprise Linux Platform is the choice for Security and Compliance in IT
Organizations tend to limit the use of enterprise Linux to only critical workloads in their Linux environment while treating other workloads as secondary citizens in their IT. However, compliance and security must be considered when managing all types of workloads. SUSE Linux Enterprise Server (SLES) has a unique level of certifications and a security approach that helps organizations achieve a secure and reliable IT operations environment.
Introduction
In today’s digital landscape, where open-source technologies are at the core of innovation, choosing a Linux distribution goes beyond mere functionality. Enterprises are tasked with ensuring the utmost security and compliance, especially regarding critical applications, but they also must apply to internal developments and emerging deployment models like containers. This blog delves into why organizations should consider a certified Enterprise Linux, like SLES, as their default Linux distribution over free alternatives, like Debian or Ubuntu, or the use of non-curated libraries downloaded directly from community repositories, emphasizing the significance of a certification-evaluated Secure Software Supply Chain.
What is offered by an Enterprise Linux
An enterprise Linux offers more than just support and patches for Linux. It provides compliance and security as well. It gives access to a curated set of enterprise-supported open-source libraries, container images, and development tools that are essential for modern organizations. The benefits of enterprise Linux are numerous and include long life cycles that can meet the needs of any IT system. Specifically, for those systems and devices needing to be supported over decades, enterprise Linux benefits are clear because only an enterprise Linux provider like SUSE, with its unparallel Long Term Service Pack Support (LTSS) Core offering, is able to provide up to 19 years of lifecycle support for a single SLES version. Another of the most relevant benefits of an enterprise Linux distribution is security, including certifications, security patches, and vulnerability assessments among best practices and hardening guides. SUSE shows an excellent example of what to expect from such a distribution and which certifications should be expected.
Expanding Horizons of Open Source
Beyond traditional enterprise applications, open-source technologies are now foundational to containerized deployments and development workflows. However, the inherent flexibility of open-source often leads to lax security practices, with employees and departments freely utilizing “free” Linux distributions or third-party libraries and container images downloaded from community repositories without stringent oversight.
Development teams working on those scenarios that usually involve continuous delivery (CD) and continuous integration (CI), where long-term support or maintenance is not the primary concern, are more likely to undervalue the benefits of enterprise Linux. However, using a curated set of libraries, base container images, and tools provided through a certified secure software supply chain ensures the security of these components and establishes a safe and auditable foundation for development. This is becoming the only way for the organization to minimize its liability in the event of a security breach and to derisk and streamline compliance assessment and assurance, which would be critical for the business.
Furthermore, enterprise Linux providers often offer a hosted registry to simplify access to curated container images, including containers with language development environments and full and lightweight container images for container development, providing support for it. If you’re looking for a secure way to access these resources, you can check out the SUSE public-hosted registry.
Compliance needs a secure software supply chain.
Compliance regulations such as EU (NIS-2 and CRA) and US (M-22-18) now require organizations to ensure the security of their supply chains, including those of their direct providers. This responsibility requires acting with due diligence, which may involve conducting a Conformity Assessment in some instances. Essentially, companies must prove they have taken all necessary precautions to prevent security incidents in their IT services. Software Bill of Materials (SBOM), Standardized Vulnerability Handling and Reporting are now part of the minimum requirements as well as guaranteed security updates for a certain period.
Therefore, an organization is responsible for the security of its entire IT software environment, including certification and assessment of third-party software used in its IT services. This applies to the Linux operating system and all other open-source components, such as development tools, libraries, and container images.
However, this task can be complex and expensive. Qualified experts are even hard to find. Numerous liaisons with communities and circles, as well as Government Authorities, have to be set up and reliably maintained. Licenses have to be monitored, fulfilled, and carefully strategically coordinated. Hence, organizations can minimize compliance costs and potential liabilities in case of breaches by using a certified Secure Software Supply Chain software provider, like SUSE, for their Linux and open-source software and its patches. Additionally, using providers with certified procedures will minimize the occurrence of security vulnerabilities.
The Imperative Need for Enterprise-Grade Linux
Enterprise Linux is no longer an option but a necessity, particularly amidst rising cybersecurity threats. Recent events, such as the XZ vulnerability in widely used Linux software, underscore the risks inherent in solely relying on community-driven distributions.
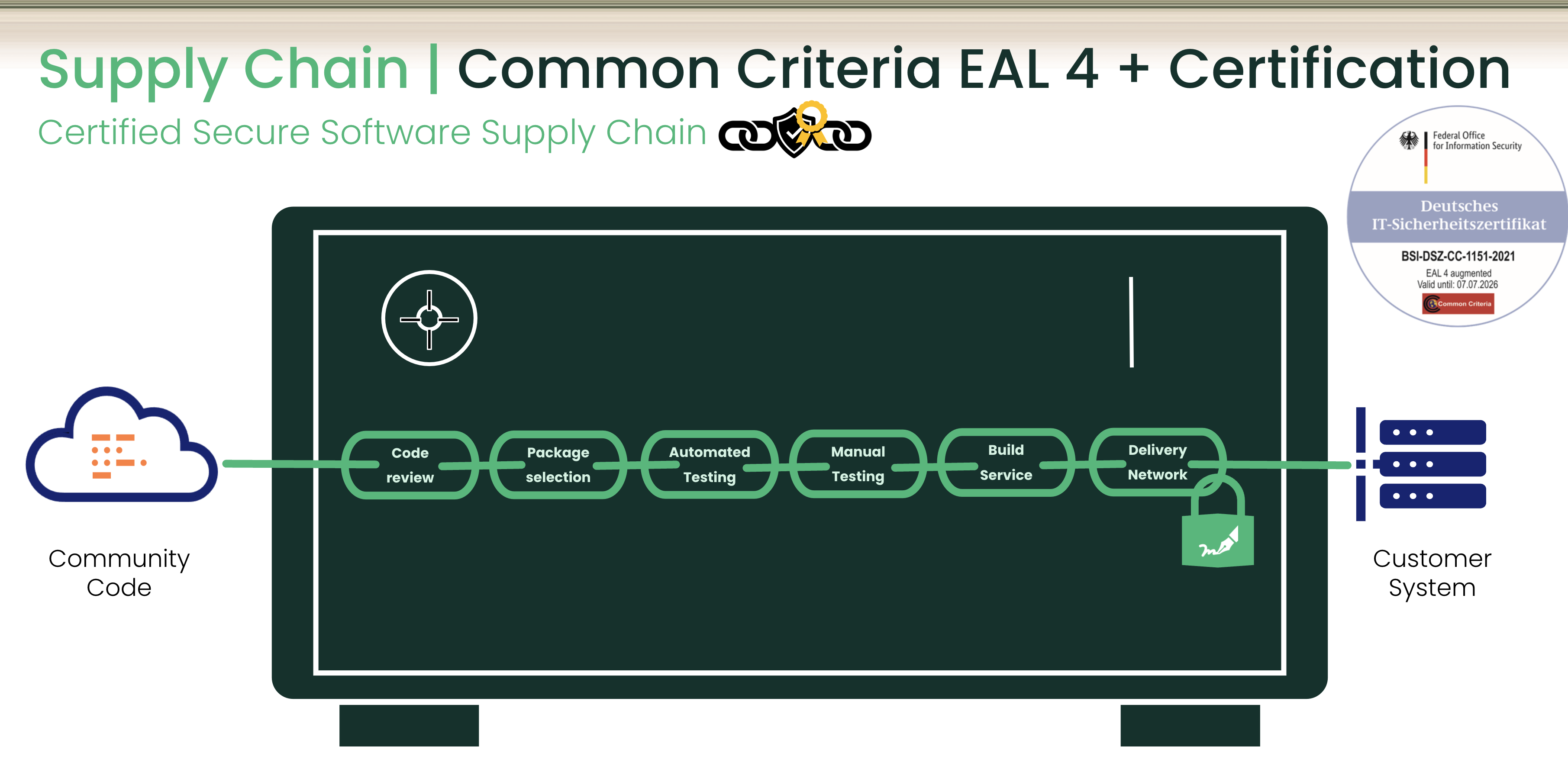
Using “free” Linux distributions, including those considered stables such as Debian or lightweight and self-defined as secure Linux distributions such as Alpine, or relying on non-curated open-source libraries poses significant challenges and risks for organizations, particularly regarding security and compliance. Unlike enterprise-grade Linux distributions like SLES, community-driven distributions often lack the rigorous security measures and certifications required for enterprise environments. For example, SLES holds unparalleled certifications like Common Criteria (CC) Evaluation Assurance Level (EAL) 4+ , which includes all necessary measures for a Secure Software Supply Chain, assuring that the operating system and associated software components adhere to stringent security protocols. By contrast, community distributions don’t undergo the same testing and security assessments, exposing organizations to potential vulnerabilities and compliance issues.
Furthermore, leveraging a certification-evaluated Secure Software Supply Chain provider like SLES can streamline compliance efforts by eliminating the need for organizations to conduct exhaustive assessments of third-party software components for which they need to have the necessary competency and are liable. This certification ensures that the software provisioning lifecycle, including patches and updates, meets state-of-the-art security standards, reducing the burden of compliance management and enhancing overall security posture. In today’s regulatory landscape, where data protection and risk mitigation are paramount, investing in an enterprise-grade Linux solution with robust security certifications is essential for maintaining operational integrity and safeguarding sensitive information.
Addressing Security Risks with SUSE Linux Enterprise Server
SUSE Linux Enterprise Server is positioned as the pinnacle of enterprise security with the highest certifications, being the only general-purpose Linux provider with a CC EAL4+ certification. Only from Evaluation Assurance Level 4 augmented by ALC_FLR.3 the entire Secure Software Supply Chain is part of the evaluation. It ensures state-of-the-art security measures throughout the software provisioning lifecycle—from initial launch to patch development and software updates. But why does this matter?
SUSE Secure Software Supply Chain CC EAL4+ image
The Importance of a Secure Software Supply Chain
In a regulatory environment where organizations bear the burden of ensuring security, SLES provides a critical safeguard. SUSE’s Secure Software Supply Chain ensures that every aspect of the software provided, including patches and updates, adheres to stringent security protocols. However, HR processes and physical access protection measures are also checked, even during site visits. This reduces the risk of vulnerabilities that can compromise critical business operations.
Ensuring Compliance and Reducing Operational Risk
Organizations that deal with sensitive data or run mission-critical applications such as SAP cannot take compliance and security lightly. SLES provides a robust framework that complies with regulatory requirements, reduces operational risk, and protects against potential breaches.
However, compliance and security are equally important for internal developments, containerized environments, and what may be considered non-critical applications. Organizations face unacceptable risks in their overall IT when they treat those as a secondary citizen in terms of security.
Conclusion
In conclusion, a certified Enterprise Linux provider can offer peace of mind and the needed stability and security in IT. The adoption of SUSE Linux Enterprise Server and its enterprise-supported container images, open-source libraries, and tools in all the company departments represents a proactive step towards enhancing security and compliance in enterprise environments. By leveraging SUSE as a certification-evaluated Secure Software Supply Chain provider, organizations can mitigate risks associated with open-source technologies, ensuring a stable and secure foundation for critical business operations. Embrace SLES to safeguard your enterprise against emerging threats and maintain the highest standards of operational integrity.
For more information on SUSE Linux Enterprise Server: https://www.suse.com/products/server/
Unlock the Easiest Path to HA SQL Server in Kubernetes
DH2i’s DxEnterprise with Rancher Prime by SUSE provides an ideal, infrastructure-agnostic, streamlined, high availability solution empowering enterprises to achieve unprecedented resilience, scalability, and security for their business-critical, Microsoft SQL Server landscapes. ~ Terry Smith
SUSE GUEST BLOG ARTICLE AUTHORED BY:
Don Boxley, Jr., co-founder and CEO of DH2i
There is no denying that containers play a pivotal role in the contemporary iteration of a “dream” SQL Server environment. Innovative organizations around the globe are leveraging containers as a vehicle to achieve cost savings and optimal resource utilization, as well as peak scalability and flexibility.
Unfortunately, inexperience with complex container orchestration technologies like Kubernetes remains a significant barrier preventing companies from being able to harness the power of containers. Downtime mitigation is also a widespread concern, as organizations aren’t even going to give containers a second thought for their business-critical SQL Server workloads if they don’t have the power to achieve “5 nines” uptime.
In this blog article we’ll further unwrap the challenges IT pros are facing in their pursuit of SQL Server containers. We’ll introduce you to how DH2i and SUSE make container modernization easier than ever before—simplifying the process all the way from initial deployment to the implementation of comprehensive high availability on the Azure Platform.
Kubernetes possesses a labyrinth of configuration complexity, and in-turn, a steep learning curve for IT pros endeavoring into the technology for the first time. It defines a complex infrastructure so that the ensuing deployment of applications can be a straightforward and efficient process.
Kubernetes’ built-in downtime mitigation functionality poses a big issue for prospective SQL Server deployments as well. While Kubernetes does provide pod-level failover in the instance of an outage, it is captive to a 5-minute minimum downtime window for pod redeployment in the instance of an interrupted workload. This inherent latency of Kubernetes renders it totally ineligible for hosting critical SQL Server workloads that need to be held to much higher “5 nines” uptime standards.
DH2i’s DxEnterprise (DxE) and Rancher Prime by SUSE deliver on the promise to make Microsoft SQL Server Kubernetes deployments easier and more approachable than ever before. This combination brings an infrastructure agnostic, streamlined solution to the table that simplifies the SQL Server container modernization process all the way from migration/deployment to advanced high availability (HA) automation and ongoing orchestration. When integrated with the Azure Kubernetes Services (AKS) platform, the DH2i and Rancher Prime solution provides seamless compatibility and enhanced functionality, allowing organizations to leverage the fullest potential of AKS for their SQL Server workloads.
DxEnterprise unlocks this unparalleled uptime with the exclusive capability of fully automatic, database-level failover for SQL Server Availability Groups (AGs) in Kubernetes, reducing failover windows from minutes to mere seconds. DxEnterprise’s included DxOperator technology fully automates SQL Server AG deployments in Kubernetes and enables unique customizability for your Kubernetes-housed AG, such as the ability to toggle between synchronous and asynchronous pod replication.
Rancher Prime by SUSE is the comprehensive management platform that helps you run Kubernetes efficiently and securely everywhere. Rancher Prime provides an easy-to-use interface, advanced automation, unified policy, security, and user management, a rich ecosystem of tools and extensions, deployment from a trusted registry, and exclusive access to professional services and support. Rancher Prime mitigates the complexities and risks of cloud-native modernization. Install Rancher Prime in your data center or in the public cloud, including Microsoft Azure for a supported, pay-as-you-go option that can manage your Kubernetes landscape everywhere.
DxEnterprise is a secure and capable clustering solution that significantly improves on the pod-level high availability provided by Kubernetes. DxEnterprise locks down your network connections with application-level Zero Trust Network Access tunnels and ensures the industry’s lowest downtime for containerized SQL Server. Bolster your security further with easy integration of SUSE’s NeuVector Prime for full lifecycle container security.
DH2i and SUSE, in collaboration with Microsoft Azure, bring together the perfect ingredients for efficient and administrator-friendly SQL Server Availability Group deployments in Kubernetes. Customers gain the security of a jointly validated, enterprise solution with peak flexibility and scalability, vastly improved resilience, and optimal resource utilization for potentially huge cost savings.
Head over to the DH2i website and download a free license so that you can test DxEnterprise and the DxOperator in your Rancher-managed Kubernetes environment for the next 30 days. Check out the quick start guide and demonstration to see how easily you can deploy an SQL Server AG in AKS with DxOperator and Rancher Prime.
Here are some additional resources to help you get the most out of your trial period:
- Always-Secure, Always-On: Rancher + Helm Availability Groups demonstration
- Modernize SQL Server with Kubernetes with DH2i and SUSE demonstration
- Getting started with Rancher by SUSE

Don Boxley, Jr. is DH2i’s co-founder and CEO. Prior to DH2i, Don spent more than 20 years in management positions for leading technology companies, including Hewlett-Packard, CoCreate Software, Iomega, and Colorado Memory Systems. Don earned his MBA from the Johnson School of Management, Cornell University.
SUSE’s Container Security Platform Now Listed in Amazon EKS Best Practices: A Big Step for Container Security
Thanks to our collaboration with AWS and work from Dominik Wombacher, we’re thrilled to announce that SUSE’s Container Security Platform, NeuVector Prime, is now recognized in the official Amazon EKS Best Practices documentation across six key security areas:
-
This inclusion signifies a significant step forward in the collaboration between AWS and SUSE on bolstering container security.
NeuVector Prime is the only 100% open-source, Kubernetes-native security platform. It safeguards your EKS workloads with eight distinct security functions, encompassing both supply chain vulnerability scanning and complete run-time protection for containers, pods, and hosts, including:
- CI/CD Vulnerability Management & Admission Control. Scan images with a Jenkins plug-in, scan registries, and enforce admission control rules for deployments into production.
- Violation Protection. Discovers behavior and creates a whitelist based policy to detect violations of normal behavior.
- Threat Detection. Detects common application attacks such as DDoS and DNS attacks on containers.
- DLP and WAF Sensors. Inspect network traffic for Data Loss Prevention of sensitive data, and detect common OWASP Top10 WAF attacks.
- Run-time Vulnerability Scanning. Scans registries, images and running containers orchestration platforms and hosts for common (CVE) as well as application specific vulnerabilities.
- Compliance & Auditing. Runs Docker Bench tests and Kubernetes CIS Benchmarks automatically.
- Endpoint/Host Security. Detects privilege escalations, monitors processes and file activity on hosts and within containers, and monitors container file systems for suspicious activity.
- Multi-cluster Management. Monitor and manage multiple Kubernetes clusters from a single console.
A key differentiator is NeuVector Prime’s patented network Deep Packet Inspection (DPI) technology. This enables not only runtime network threat detection but also automates Zero Trust network micro-segmentation and Data Loss Prevention (DLP) within your Kubernetes environment.
By combining these runtime layers with supply chain layers featuring vulnerability management and admission control, NeuVector Prime empowers users to:
- Rapidly strengthen security posture: Achieve a robust security stance in under an hour.
- Automate Zero Trust security-as-code: Simplify security implementation and management. Implement this into your existing CI pipeline.
- Identify live attacks and safeguard applications: Protect against zero-day attacks, unpatched vulnerabilities, and insider threats.
The EKS Security Best Practices provides guidance on hardening your EKS microservice infrastructure and mitigating threats through a security in-depth approach. NeuVector Prime functions at the center of this approach.
NeuVector Prime simplifies security for AWS deployments, offering the following advantages:
- Compliance made easy: Achieve compliance with industry standards like PCI, GDPR, SOC 2, HIPAA, and NIST. NeuVector Prime helps meet these requirements through features like network segmentation, vulnerability scanning, configuration auditing, access controls, and data encryption.
- Automated security for peace of mind: NeuVector Prime automatically discovers containers, learns application behavior, and creates security policies to shield them from anomalies, threats and vulnerabilities. Additionally, real-time security event logging provides continuous visibility into container traffic.
- Seamless scaling with Amazon EKS: NeuVector Prime seamlessly integrates with Amazon EKS scaling features. As your applications evolve, NeuVector automatically adapts to safeguard your containerized environment.
- NeuVector Prime functions as a network tap: NeuVector Prime maintains its own source of truth, independent of AWS services, and also connects to Amazon Cloudwatch and other services as part of an in-depth defense approach to securing your microservice infrastructure. Neuvector Prime is the only solution allowing you to analyze and block East-West traffic within your EKS clusters, including zero-day attacks and DLP.
- NeuVector Prime installs as a k8s native application into EKS across your enterprise and Federates for centralized control.
Take Your Container Security to the Next Level:
- Register for a NeuVector Rodeo Workshop: Gain hands-on experience deploying, configuring, and operating NeuVector Prime with a free 90-minute workshop.
- Experience NeuVector Prime at re:Inforce 2024: Visit our booth #1101 for a live demo and see NeuVector Prime on Amazon EKS in action.
- Explore NeuVector Prime on the Amazon Marketplace: Learn more about NeuVector Prime and its integration with AWS.
Harnessing AI in Rancher Prime 3.0: Shaping the Future Together
The complexities of Kubernetes management can be overwhelming, but you don’t have to face them alone. Discover how Rancher Prime’s AI Assistant can help enterprises navigate their container orchestration journey. Rancher Prime, known for its cutting-edge container management solutions, is once again at the forefront with its AI Assistant. This powerful tool is currently in General Availability (GA) and under continued development with the valuable input of our enterprise customers.
The AI Assistant: a game-changer for Kubernetes management
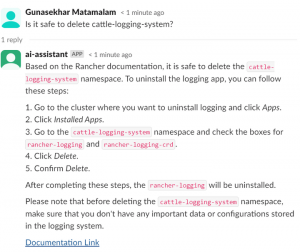
The AI Assistant is designed to simplify and enhance the Kubernetes management experience. It utilizes Retrieval-Augmented Generation (RAG) and OpenAI, leveraging our extensive documentation and knowledge base to provide timely and relevant information. RAG combines the retrieval of relevant documents with a generative model to produce responses that are both informed and contextually appropriate. When a user makes a query, the AI Assistant first searches our internal knowledgebase and then, if required, extends its search to the internet via Bing, ensuring comprehensive and up-to-date responses.
Users engage with the AI Assistant through a dedicated Slack channel, ensuring seamless and user-friendly interaction. This direct line of communication allows for real-time assistance and support, making Kubernetes management more efficient and intuitive. The objective of the AI Assistant is to assist with troubleshooting, training and inquiries, making it a versatile asset for any team.
Shaping the future together
Rancher Prime is an exclusive opportunity to experience and influence the development of the AI Assistant. While we’re not actively inviting new participants, our sales team may extend invites to interested customers. This collaborative approach ensures that the final product will meet the high standards and specific needs of our enterprise customers.
The Rancher Prime AI Assistant represents a significant leap forward in Kubernetes management. By providing an intelligent, user-friendly tool, we’re empowering our customers to manage their containerized environments with greater ease and efficiency. Stay tuned for further updates as we continue to refine and enhance this exciting new feature.
Ready to transform your Kubernetes management experience?
Explore the future of container orchestration with Rancher Prime 3.0 and be part of shaping the AI Assistant that’s designed to empower your enterprise teams.
For more information If you don’t have Rancher Prime contact a Solutions expert today. If you’re an existing customer and interested, contact your representative.
Install your HPC Cluster with Warewulf
Preface
In High Performance Computing (HPC), computing tasks are usually distributed among many compute threads which are spread across multiples cores, sockets and machines (nodes). These threads are tightly coupled together. Therefore, compute clusters consist of a number of largely identical machines that need to be managed to maintain a well-defined and identical setup across all nodes. Once clusters scale up, there are many scalability factors to overcome. Warewulf is there to address this ‘administrative scaling’.
Warewulf is an operating system-agnostic installation and management system for HPC clusters.
It is quick and easy to learn and use as many settings are pre-configured to sensible defaults. Also, it still provides the flexibility allowing fine tuning the configuration to local needs. It is released under the BSD license, its source code is available at https://github.com/warewulf/warewulf. This is where the development happens as well.
This article gives an overview on how to set up Warewulf on SUSE Linux Enterprise High Performance Computing (SLE HPC) 15 SP5 or later.
Installing Warewulf
Compute clusters consist of at least one management (or head) node which is usually multi-homed: connected both to an external network and a cluster private network, as well as multiple compute nodes which reside solely on the private network. Other private networks dedicated to high speed tasks like RDMA and storage access may exist as well. Warewulf gets installed on one of the management nodes of a cluster to manage and oversee the installation and management of the compute nodes.
To install Warewulf on a cluster which is running SLE HPC 15 SP5 or later, simply run:
zypper install warewulf
This package seamlessly integrates into a SUSE system and should therefore be preferred over packages provided on Github.
During the installation, the actual network configuration is written to /etc/warewulf/warewulf.conf. These settings should be verified, as for multi homed hosts a sensible pre-configuration is not always possible.
Setting up the network configuration
Check /etc/warewulf/warewulf.conf for the following values:
ipaddr: 172.16.16.250
netmask: 255.255.255.0
network: 172.16.16.0
where ipaddr should be the IP address of this management host. Also check the values of netmask and network – these should match this network.
Additionally, you may want to configure the IP address range for dynamic/unknown hosts:
dhcp:
range start: 172.16.26.21
range end: 172.16.26.50
If the ISC DHCP server (dhcpd) is used (default on SUSE), make sure the value of DHCPD_INTERFACE in the file /etc/sysconfig/dhcpd has been set to the correct value.
Starting warewulf service
You are now ready to start the warewulfd service itself which delivers the images to the nodes:
systemctl enable --now warewulfd.service
Now, wwctl can be used to configure the the remaining services needed by Warewulf. Run:
wwctl configure --all
which will configure all Warewulf related services.
To conveniently log into compute nodes, you should now log out of and back into the Warewulf host, as this will create an ssh key on the Warewulf host which allows password-less login to the compute nodes. Note however, that this key is not yet pass-phrase protected. If you require protecting your private key by a pass phrase, it is probably a good idea to do so now:
ssh-keygen -p -f $HOME/.ssh/cluster
Adding nodes and profiles to Warewulf
Warewulf uses the concept of profiles which hold the generalized settings of the individual nodes. It comes with a predefined profile default, to which all new node will be assigned, if not set otherwise. You may obtain the values of the default profile with:
wwctl profile list default
Now, a node can be added with the command assigning it an IP address:
wwctl node add node01 -I 172.16.16.101
if the MAC address is known for this node, you can specify this as well:
wwctl node add node01 -I 172.16.16.101 -H cc:aa:ff:ff:ee
For adding several nodes at once you may also use a node range, e.g.
wwctl node add node[01-10] -I 172.16.16.101
This will add the nodes with ip addresses starting at the specified address and incremented by Warewulf.
Importing a container
Warewulf uses a special container[1] as base to build OS images for the compute nodes. This is self contained and independent of the operating system installed on the Warewulf host. For SLE HPC customers, SUSE provides a fully supported SLE HPC node image[2].
To import a SLE HPC SP5 node container set your SCC credentials in environment variables and run:
export WAREWULF_OCI_USERNAME=myemail@example.com
export WAREWULF_OCI_PASSWORD=MY_SCC_PASSCODE
wwctl container import registry.suse.com/suse/hpc/warewulf4-x86_64/sle-hpc-node:15.5 --setdefault
(Replace myemail@example.com and MY_SCC_PASSWORD with the credentials used for your subscription.)
This will import the specified container for the default profile.
Furthermore, it is also possible to import an image from a local installation into a directory by using the path to this directory (chroot directory) as argument for wwctl import.
Booting nodes
As a final preparation you should rebuild the container image, now, by running:
wwctl container build leap15.5
as well as all the configuration overlays with the command:
wwctl overlay build
just in case the build of the image may have failed earlier due to an error. If you didn’t assign a hardware address to a node before, you should set the node into the discoverable state before powering it on. This is done with:
wwctl node set node01 --discoverable
Also you should run:
wwctl configure hostlist
to add the new nodes to the file /etc/hosts. Now, you should make sure that the node(s) will boot over PXE from the network interface connected to the specified network and power on the node(s) to boot into assigned image.
Additional configuration
The configuration files for the nodes are managed as Golang text templates. The resulting files are overlayed over the node images. There are two ways of transport for the overlays to the compute node:
- the system overlay which is ‘baked’ into the image during boot as part of the
wwinitprocess. - the runtime overlay which is updated on the nodes on a regular base (1 minute per default) via the
wwclientservice.
n the default configuration the overlay called wwinit is used as system overlay. You may list the files in this overlays with the command:
wwctl overlay list wwinit -a
which will show a list of all the files in the overlays. Files ending with the suffix .ww are interpreted as template by Warewulf, the suffix is removed in the rendered overlay. To inspect the content of an overlay use the command:
wwctl overlay show wwinit /etc/issue.wwTo render the template using the values for node01 use:
wwctl overlay show wwinit /etc/issue.ww -r node01The overlay template itself may be edited using the command:
wwctl overlay edit wwinit /etc/issue.ww
Please note that after editing templates, the overlays aren’t updated automatically and you should trigger a rebuild with the command:
wwctl overlay build
The variables available in a template can be listed with:
wwctl overlay show debug /warewulf/template-variables.md.ww
Modifying the container
The node container is a self contained operating system image. You can open a shell in the image with the command:
wwctl container shell leap15.5
After you have opened a shell, you may install additional software using zypper.
The shell command provides the option --bind which allows mounting arbitrary host directories into the container during the shell session.
Please note that if a command exits with a non-zero status, the image won’t be rebuilt automatically. Therefore, it is advised to rebuild the container with:
wwctl conainer build leap15.5
after any change.
Network configuration
Warewulf allows configuring multiple network interfaces for the compute nodes. Therefore, you can add another network interface for example for infiniband using the command:
wwctl node set node01 --netname infininet -I 172.16.17.101 --netdev ib0 --mtu 9000 --type infiniband
This will add the infiniband interface ib0 to the node node01. You can now list the network interfaces of the node:
wwctl node list -n
As changes in the settings are not propagated to all configuration files, the node overlays should be rebuilt after this change by running the command:
wwctl overlay build
After a reboot, these changes will be present on the nodes; in the above case the Infiniband interface will be active on the node.
A more elegant way to get the same result is to create a profile to hold all those values which are identical for all interfaces. In this case, these are mtu and netdev. Create anew profile for an Infiniband network using the command:
wwctl profile add infiniband-nodes --netname infininet --netdev ib0 --mtu 9000 --type infiniband
You may now add this profile to a node and remove the node specific settings which are now part of the common profile by executing:
wwctl node set node01 --netname infininet --netdev UNDEF --mtu UNDEF --type UNDEF --profiles default,infiniband-nodes
To list the data in a profile use the command:
wwctl profile list -A infiniband-nodes
Secure Boot
Switch to grub boot
By default, Warewulf boots nodes via iPXE, which isn’t signed by SUSE and can’t be used when secure boot is enabled. In order to switch to grub as the boot method you must add or change the following value in /etc/warewulf/warewulf.conf:
warewulf:
grubboot: true
After this change, you will have to reconfigure dhcpd and tftp executing:
wwctl configure dhcp
wwctl configure tftp
and rebuild the overlays with the command:
wwctl overlay build
Also make sure that the packages shim and grub2-x86_64-efi (for x86-64) or grub2-arm64-efi (for aarch64) are installed in the container. shim is required by secure boot.
[1]This container is special only in that it is bootable, i.e. it contains a kernel and an init-implementation (i.e. systemd) (Go Back)
[2]You will find node containers with ‘community support’ which do not require a subscription at registry.opensuse.org/science/warewulf/leap-15.5/containers/kernel:latest.
A blog post describing the installation and setup of Warewulf on openSUSE Leap and Tumbleweed can be found here. (Go Back)
How NeuVector Can Protect Against the XZ Backdoor Attack CVE-2024-3094 in Kubernetes Environments
Security researcher Andres Freund reported to Debian that the xz/liblzma library had been backdoored. As a result, CVE-2024-3094 was published with a critical CVSS score of 10. This vulnerability stems from a supply chain compromise on versions 5.6.0 and 5.6.1 of XZ Utils. XZ Utils is data compression software included in major Linux distributions. The recommended action is to downgrade to an uncompromised XZ Utils version (earlier than 5.6.0).
Detecting CVE-2024-3094
NeuVector, the 100% open source, full-lifecycle container security solution from SUSE, is able to scan for and detect CVE-2024-3094 in its vulnerability scanner starting with CVE Database Version 3.395, created 03/31/2024. Scanning images, running containers and scanning the hosts on which they run are some of the actionable steps that can be taken to protect against this exploitation. Any detected vulnerabilities should be remediated immediately; some pipelines may take some time to redeploy a remediated image.
Detecting and preventing exploits
NeuVector provides zero trust runtime security designed to detect and prevent zero-day attacks as well as exploits of unknown or unpatched vulnerabilities in Kubernetes and other containerized environments, as well as the hosts* on which they run. NeuVector run-time protections include:
- General zero trust network controls will not allow unauthorized inbound or outbound ssh connections. Should a compromise occur, these network controls will also help detect follow-on (i.e., ‘kill chain’) activities to expand the blast radius of the attack, such as probing for sensitive data.
- Zero trust egress controls are the most effective way to prevent command and control exploitations. Make sure aggressive egress controls are in place with Protect mode (blocking) enabled in NeuVector for any containers with external access or with this CVE detected. By default, allowing listed legitimate external connections will prevent unauthorized SSH connections. However, an added layer of protection could be implemented to block external SSH connections explicitly.
- Built-in suspicious process detection for process activity is typically not expected in running containers, such as sshd for inbound and ssh for outbound connections. Ensure that alerting is properly configured for when these suspicious activities are detected, and consider Protect mode for affected containers to block these processes.
- Additional protections should be considered in NeuVector:
- Add an Admission Control rule to block any deployments of images with CVE-2024-3094.
- Implement Protect mode for any containers with potential exposure to ensure:
- No egress/external connections are in the “allowlist.”
- External connections are explicitly allowed to specific DNS hostnames and IP addresses and for only required application protocol(s).
- Enforce supply chain security by vetting and approving image sources and requiring signatures to be verified by admission controls before deploying.
*NeuVector scans hosts and nodes for vulnerabilities and detects suspicious processes. Network firewall protections apply only to container workloads.
The NeuVector container security platform software and its containers themselves are not vulnerable to this exploit. Customers using SUSE’s enterprise-supported container security, NeuVector Prime, can contact SUSE Support for additional questions or advice regarding protecting against this exploit.
Want to learn more?
SUSE addressed this vulnerability in a recent blog post and openSUSE announcement, indicating that SUSE Linux Enterprise and Leap are also unaffected by this backdoor.
5 Reasons Why Linux Choice Matters
 SUSE’s open source ethos has always been about choice, transparency and community. SUSE released its first enterprise Linux distro over 30 years ago. And we’ve been managing multi Linux distributions for over 20 years with SUSE Manager. It is also why SUSE released SUSE Liberty Linux. SUSE Liberty Linux is a technology and solutions offering that lets you keep your desired Linux OS (CentOS or RHEL) and get your security patches, maintenance updates and technical support from SUSE. In today’s open source landscape, this is particularly important – especially if you are running a Linux distro that is rapidly reaching end of life.
SUSE’s open source ethos has always been about choice, transparency and community. SUSE released its first enterprise Linux distro over 30 years ago. And we’ve been managing multi Linux distributions for over 20 years with SUSE Manager. It is also why SUSE released SUSE Liberty Linux. SUSE Liberty Linux is a technology and solutions offering that lets you keep your desired Linux OS (CentOS or RHEL) and get your security patches, maintenance updates and technical support from SUSE. In today’s open source landscape, this is particularly important – especially if you are running a Linux distro that is rapidly reaching end of life.
You might be thinking, “There are a number of distros that I can choose from, why should I choose SUSE Liberty Linux?” Here are 5 very good reasons why SUSE Liberty Linux should be at the top of your list.
Zero migration
Choosing SUSE Liberty Linux means that Jul 1, 2024 is just another day in your data center. SUSE Liberty Linux is a technology and support solution that lets you continue using the RHEL 7 and CentOS workloads you already have, while providing you with a unified support experience for managing your heterogeneous IT environments. This means zero risky migrations, zero retraining, and zero disruptions. And because we know how priceless security is to your data center, we proactively provide CVE security patches and maintenance updates on a regular cadence. So when considering other options, consider the cost of migration, retraining and retesting – then consider SUSE Liberty Linux.
Full compatibility
SUSE Liberty Linux is fully compatible on the application binary interface level with the versions of RHEL currently supported and available today, and with CentOS. User-space applications that run on RHEL or CentOS are expected to run with equivalent performance and functionality on SUSE Liberty Linux.*
We backport fixes into the CentOS code, the same way we do with our own software—keeping 100% compatibility of API and application binary interface (ABI). We’re fixing the vulnerabilities you have without breaking anything. We’ve done this for decades. Now, we’re happy to do it for you.
User-space applications that run on RHEL are expected to run with equivalent performance and functionality on SUSE Liberty Linux. Factors in each customer’s environment will impact the performance of the OS and the applications and so we advise customers to thoroughly test their specific applications on their OS prior to running production workloads.
SUSE stands behind its SUSE Liberty Linux offering to the same degree we do all our products and has decades’ experience in assisting customers migrate between, and manage, different enterprise Linux workloads.
* Factors in each customer’s environment will impact the performance of the OS and the applications and so we advise customers to thoroughly test their specific applications on their OS prior to running production workloads.
Backed by SUSE
SUSE Liberty Linux is backed by SUSE. SUSE is the company that released the very first Linux distribution way back in 1992. That means for more than 30 years SUSE has been the vanguard of open source technologies.
SUSE has an impressive bench of software engineers that eat, breathe, and sleep open source. We are heavily involved and contribute to the open source communities on a regular basis. We believe in transparency and openness and we will not only adhere to the letter of the open source but also the spirit of openness. You have the right to have a choice; we’re here to support you.
Support for your entire infrastructure
SUSE makes Linux, but we manage multiple Linuxes. We understand that heterogeneity is the reality in most businesses. But managing and supporting a heterogeneous Linux environment can be hard, complex and time consuming. SUSE has simplified this:
- With SUSE Manager that manages over 16 different Linux distros from a single pane of glass.
- With a world-class support team that provides support for not only our SLES, but also for your other distros.
- With optional support services that provide a named premium support resource for your entire infrastructure.
Services that lead to success
SUSE Global Services has the expertise to help you navigate the open source landscape. Whether you choose to transition to SUSE Liberty Linux or migrate to SLES, we have the expertise available to ensure your transition is a success. Just some of the services we offer are:
- Premium Support Services provides you with direct access to a named engineer that can support your entire environment, including RHEL, CentOS, SLES and Liberty.
- Consulting engagements to optimize your transition to Liberty. These range in scope from validating the health of your current infrastructure to implementing solutions to simplify management of your current infrastructure through migration services to design and implement a migration to SLES.
- eLearning subscriptions that provide limitless learning opportunities for you and your team to learn about SUSE technologies on your time.
Summary
As you make your decision on what to do with your current infrastructure, consider your choices carefully. Consider SUSE Liberty Linux.
Curious to learn more? Watch the on demand webinar or reach out to your account rep today!
SUSE addresses supply chain attack against xz compression library
SUSE received notification of a supply chain attack against the “xz” compression tool and “liblzma5” library.
Background
Security Researcher Andres Freund reported to Debian that the xz / liblzma library had been backdoored.
This backdoor was introduced in the upstream github xz project with release 5.6.0 in February 2024.
For the statement from the openSUSE project please refer to https://news.opensuse.org/2024/03/29/xz-backdoor/
SUSE Linux Enterprise and Leap are built in isolation from openSUSE. Code, functionality and characteristics of Tumbleweed are not automatically introduced in SUSE Linux Enterprise and/or Leap. It has been established that the malicious file introduced into Tumbleweed is not present in SUSE Linux Enterprise and/or Leap. Additionally, SUSE has verified that SLE BCI, SUSE Rancher, SUSE Edge and SUSE Liberty Linux products or offerings are not affected. SUSE will continue to monitor this issue, and make any updates if and as necessary.
Links