SUSE and enclaive Partner to Secure the Cloud Crypto Perimeter with Virtual HSM Capabilities
SUSE is pleased to announce a new partnership with enclaive. This collaboration is marked by the official certification of enclaive’s Virtual Hardware Security Module (vHSM) — a groundbreaking, software-defined solution built on Confidential Computing — for operational efficiency on SUSE Rancher Prime.
The joint solution, featuring enclaive vHSM and SUSE Rancher Prime, directly overcomes a major barrier to cloud adoption: the critical ability to maintain complete and verifiable control over their master encryption keys at scale. Importantly, organizations can achieve this level of security without modifying existing applications — the vHSM integrates seamlessly into current infrastructure, eliminating costly and time-consuming code rewrites.
As European organisations accelerate their transition to the cloud, digital sovereignty has become an essential requirement. They want the flexibility and efficiency of modern cloud platforms, but only if they retain full control over their most sensitive information — especially cryptographic keys. Traditional Hardware Security Modules (HSMs), once the standard for securing such keys, cannot match the scalability and agility required in today’s distributed cloud environments. Virtual HSMs (vHSMs) meet this need by delivering hardware-grade key protection in a scalable, software-based form, seamlessly fitting into sovereign-cloud and multi-cloud architectures.
At the same time, classic encryption — of data in transit and data at rest — still leaves a major gap: data becomes exposed when it is processed. Confidential Computing closes this gap by running workloads inside secure, isolated enclaves, keeping data in use protected — even from privileged system layers or cloud administrators. In a nutshell, Confidential Computing protects and encrypts data also while it is being processed. It leverages Trusted Execution Environments (TEEs) to isolate workloads and cryptographic keys, and uses remote attestation to verify that code is running securely in these confidential enclaves.
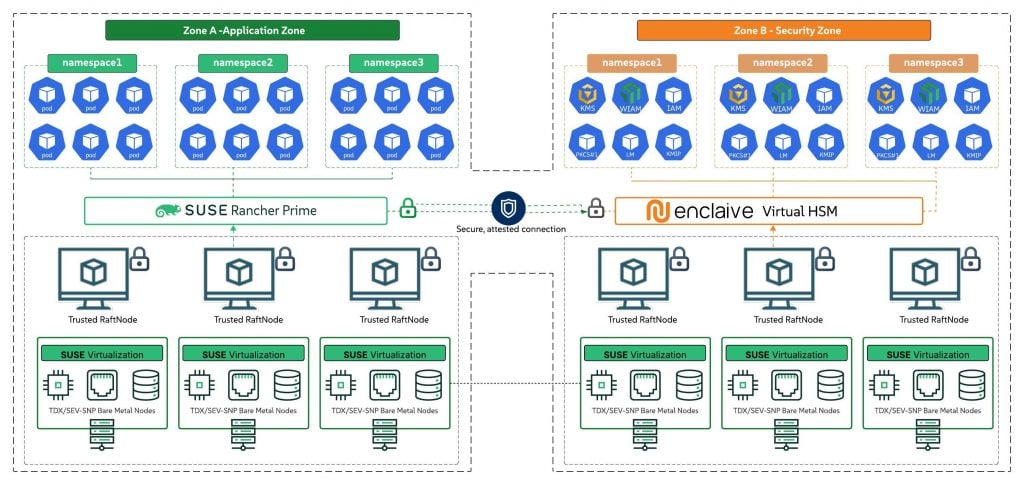
In cloud native environments, Kubernetes organises applications into pods, the smallest deployable units that can run across nodes in a cluster. SUSE Rancher Prime provides a unified, open source platform to manage these clusters efficiently, allowing organisations to deploy, monitor, and scale workloads across on-premises, hybrid, or sovereign clouds.
Inside this architecture, enclaive’s vHSM runs entirely within a TEE, ensuring that cryptographic keys and operations remain fully protected while in use. By isolating keys within secure enclaves, the vHSM guarantees that only the customer — or a trusted European entity — retains exclusive control, a cornerstone of digital sovereignty. To ensure long-term data sovereignty, the vHSM enables Post-Quantum-secure encryption, which protects sensitive data against future threats from quantum computers capable of breaking current RSA/ECC standards.
Building on this advanced cryptographic foundation, enclaive’s complementary confidential-container solution, Dyneemes, brings hardware-enforced TEE isolation directly to the pod level for the first time. This ensures that even cluster operators and infrastructure administrators are strictly prevented from accessing or tampering with running workloads. This capability enables Kubernetes to be operated in regulated environments where operational management must remain separate from access to sensitive data and cryptographic material. The result is granular, verifiable security for dynamic, containerised workloads — without compromising agility, scalability, or operational flexibility.
This is the context in which the partnership between SUSE and enclaive stands out. SUSE brings a long-standing commitment to open source technologies rooted in Europe, with transparent, vendor-neutral tooling that aligns naturally with European sovereignty goals. Its Kubernetes platform, SUSE Rancher Prime, is built on open standards and avoids proprietary lock-in — an important factor for institutions seeking independence and long-term trust. Combined with enclaive’s unique vHSM with true pod-level isolation, organisations gain an architecture that is cloud native, sovereign, and entirely under their control.
This combined approach also aligns closely with the requirements of European frameworks such as GDPR, DORA, NIS2, and the upcoming EUCS, where sovereignty, data residency, and strict control over cryptographic material are central. Together, SUSE and enclaive enable European organisations to embrace the cloud with confidence — leveraging flexible open source software, hardware-backed Confidential Computing, and verifiable secrets sovereignty, all anchored in a European technological foundation.
For more information, please visit enclaive website: https://www.enclaive.io/virtual-hsm
Related Articles
Sep 25th, 2024