NIS2 without panic: concrete tips and actions on how to improve it.
The noise is getting louder
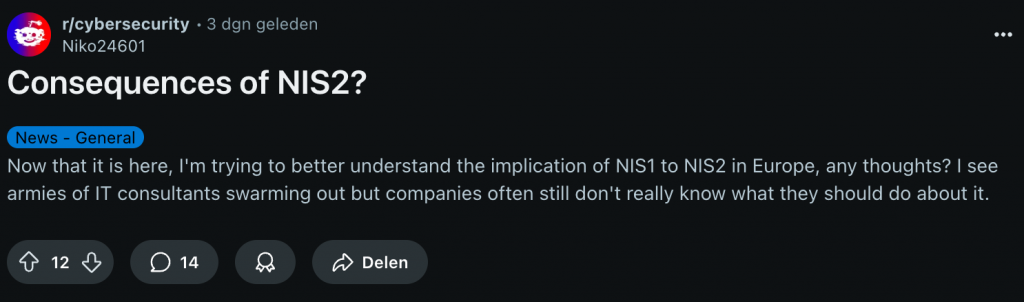
If you’ve been scanning security and compliance topics on Reddit lately, you’ve probably noticed a shift. On Reddit this week, threads about NIS2 were filled with comments like:
“We still don’t know who’s going to audit us.”
“If my SaaS provider asks me for NIS2 proof, what do I even send?”
“Our lawyers can’t agree if we’re in scope or not.”
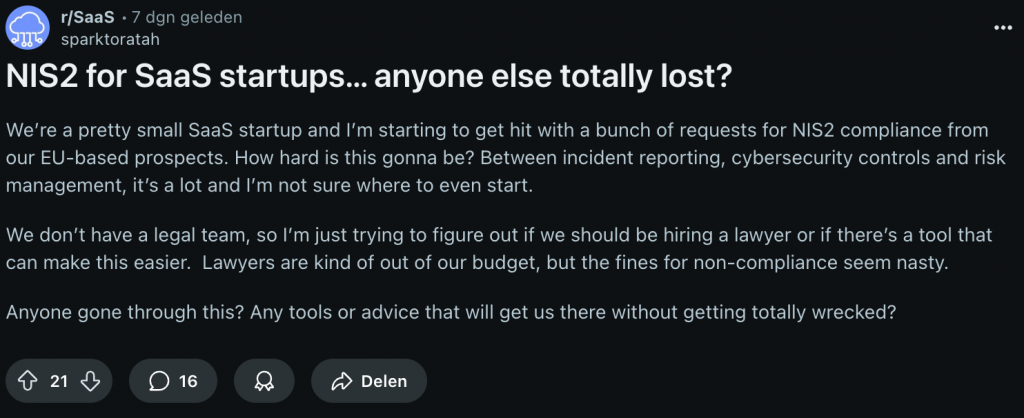
Source: https://www.reddit.com/r/SaaS/comments/1mjufxa/nis2_for_saas_startups_anyone_else_totally_lost/
This confusion is real and it’s not limited to subject-matter experts. Even in large enterprises with dedicated security teams might still be unclear on scope, timelines and how to prove compliance.
This article provides a structured checklist senior IT leaders can use to build a provable NIS2 compliance posture in 90 days.
1. Scope Check in Two Minutes
Before investing resources, confirm whether you are in scope:
- Sector: Annex I (energy, transport, finance, healthcare, etc.) or Annex II (digital infrastructure, manufacturing, space, postal, etc.)1.
- Size: Over 50 staff or €10M annual turnover → likely in scope.
- Special Case: Cloud, data center and managed service providers are in scope regardless of size.
- HQ Location: Europe
Even if you haven’t heard about it, NIS2 might still apply to your organization. Your focus could be on other regulations like CRA or DORA, but much of this article’s content remains relevant.
It’s also possible that others in your organization are already addressing compliance, perhaps under a different name if your organization has a strong existing compliance framework.
Finally, if your organization is behind, consult your CISO or senior IT leaders to understand their progress on this journey. Almost any company who is depending on their IT as a critical factor should comply? When I present at, for example, a conference and I ask for a hand, the results are surprising: Many hands go up.
2. What Auditors Will Ask First
When the audit starts, expect three immediate checks:
- Reporting readiness: Can you issue an early warning in 24 hours and a full incident notification in 72 hours?
- Policies on record: Four documented policies, incident handling, supply chain security, security testing and effectiveness review.
Evidence samples: Asset inventory, patch records and access control logs. This is the proof of the elements mentioned under 2.
3. Why Waiting is Risky
About 14 of the 27 EU member states have completed NIS2 transposition2. But the Implementing Regulation is active in all EU states now. That means if a major incident occurs today, regulators can request your reporting process, evidence and proof of compliance regardless of your local legal status.
Penalties reach up to €10M or 2% of worldwide turnover for essential entities, next to this under NIS2 executives can be held personally liable for the company’s failure to adopt particular measures.
Chapters 4 and 5 should be seen as two sides of the same coin. On the one side, policies and processes define accountability, reporting chains and the rules you operate under. On the other side, technology enforces those rules in practice, providing the guardrails and evidence you need. Both influence how people actually work day to-day, from how incidents are reported to how engineers ship software. Together, they turn abstract regulation into practical action.

Policies and Processes badge
4. The NIS2 Checklist
To streamline your process and policy development, the following five categories offer a clear roadmap of essential areas. These encompass process and responsibility definition, evidence collection for actions taken, and the implementation of relevant technologies.
Governance & Accountability
- Appoint an executive-level compliance owner
Advice: Regulators expect named accountability. Make sure responsibility sits at the right level, not buried in operations. - Draft and approve four core policies (incident handling, supply chain security, security testing, effectiveness review)
Advice: Keep them short and auditable, they’ll be the first thing an auditor asks for. - Run a 24h/72h incident reporting simulation
Advice: Test your reporting chain now. A dry run uncovers gaps in communication and documentation before a real crisis.
Software Supply Chain Security
- Sign all container images with Sigstore Cosign
Advice: This proves provenance and aligns with EU supply chain requirements. - Generate SBOMs and scan vulnerabilities with Trivy
Advice: Trivy gives you both an SBOM (“ingredient list”) and a vulnerability scan in one step. This reduces audit friction while also showing where patching is needed. - Centralize container image distribution (through the SUSE Private Registry)
Advice: A secure, EU-hostable registry provides evidence of integrity and enables CVE scanning. - Enforce admission policies with Kubewarden
Advice: Block non-compliant workloads at deployment. This is a fast way to move from “trust” to “verify.”
Runtime Security & Operations
- Harden cluster identities and access controls
Advice: SUSE Rancher Manager can help you with the must-have Role-based access and least privileges. - Segment networks and enable central logging
Advice: Logs are key evidence in incident reports. Segmentation limits breach impact. - Deploy SUSE Observability with eBPF
Advice: Real-time dependency mapping, automated issue the detection and concrete remediation guides, shortens incident response time. - Use K3s for sensitive edge or OT workloads
Advice: Minimal footprint, hardened runtime, ideal for regulated or remote environments.
Enterprise-Scale Management
- Leverage SUSE Linux Enterprise
Advice: Pre-hardened, government certified operating systems, SBOMs included reduce supply chain risk and are vital in proving compliance. - Manage multi-cluster governance with SUSE Rancher Manager
Advice: Centralize compliance, RBAC and audit trails across hybrid and multi-cloud, auditors prefer one view. - Leverage SUSE Application Collection
Advice: Pre-hardened, SBOM-ready workloads reduce supply chain risk and can accelerate engineering teams in getting applications out to production.
Evidence & Reporting
- Prepare an “auditor pack”
Contents: Policies, asset inventories, CI/CD logs or screenshots, SBOM examples, admission rules, and last incident drill notes. Having this ready means you can respond to regulator or customer requests in days, not weeks.
This checklist is there to help you understand the impact and various areas you should pay attention to. It is not an exhaustive list of what needs to happen. NIS2 but also CRA and DORA have their own requirements.
5. Your NIS2-Ready Open Source Stack
When faced with the task of implementing new features, it’s common to feel unsure about where to begin. The table below offers a concise overview of potential open-source tools that can help engineering teams tackle various aspects of the NIS2 puzzle. These tools are intended to inspire and guide efforts toward improving compliance and business resilience.
| Objective | Tool | Why It Works for NIS2 |
| Provenance & signing | Sigstore Cosign | Meets supply chain integrity requirements by cryptographically signing artifacts |
| SBOM generation/ vulnerability scanning | Trivy | Generates SBOMs in SPDX or CycloneDX format while also scanning for vulnerabilities, giving you both transparency and actionable security data in one step. |
| Certified operating systems | SUSE Linux Enterprise | Enterprise operating systems with government certifications up to Common Criteria/EAL4+, highest level supply chain security and provenance, support and life cycle commitments |
| Secure registry & evidence storage | SUSE Private Registry (Harbor) | EU-hostable registry with signature storage and SBOM generation to prove image integrity, and with CVE scanning to detect vulnerabilities |
| Policy enforcement | Kubewarden | Blocks non-compliant workloads at admission, ensuring only signed and SBOM-complete images are deployed |
| Runtime monitoring & anomaly detection | SUSE Observability (eBPF) | Provides real-time, kernel-level insight into workloads, enabling rapid incident detection and reporting |
| Minimal secure runtime for sensitive environments | K3s | Lightweight, hardened Kubernetes for edge and operational technology zones, reducing attack surface |
| Enterprise Kubernetes lifecycle management | SUSE Rancher Manager | Centralizes multi-cluster governance, policy enforcement, and audit trail collection across hybrid and multi-cloud setups |
| Curated, secure workloads | SUSE Application Collection | Provides pre-hardened, supported application images and Helm charts with SBOMs, reducing supply chain risk and audit complexity |
Your Path to Digital Sovereignty with SUSE
NIS2 doesn’t have to be overwhelming. By breaking it down into clear steps, focusing on the evidence auditors actually request and using proven open source tools, you can move from uncertainty to control. The regulations may feel complex, but the path forward is practical: define ownership, document the essentials, enforce policies, and prepare your auditor pack. Starting now not only reduces compliance risk but also strengthens the resilience of your business.
Having worked as an IT manager at ING, I know firsthand how heavy the lifting of compliance can be. Implementing new processes while keeping systems running, preparing for audits that dig deep into your IT estate and development pipelines, it’s real pressure on teams.
That’s why we built our Digital Sovereignty resources: to give IT leaders a practical starting point, backed by proven open source solutions. If you want to take the next step in making NIS2 compliance manageable while strengthening your organization’s resilience, visit our Digital Sovereignty page and explore how we can support you.
Sources:
- https://eur-lex.europa.eu/legal-content/EN/TXT/HTML/?uri=CELEX:32022L2555#d1e32-143-1
- https://digital-strategy.ec.europa.eu/en/policies/nis-transposition
Related Articles
Oct 25th, 2024
Live Patching and Immutable System
Nov 07th, 2025